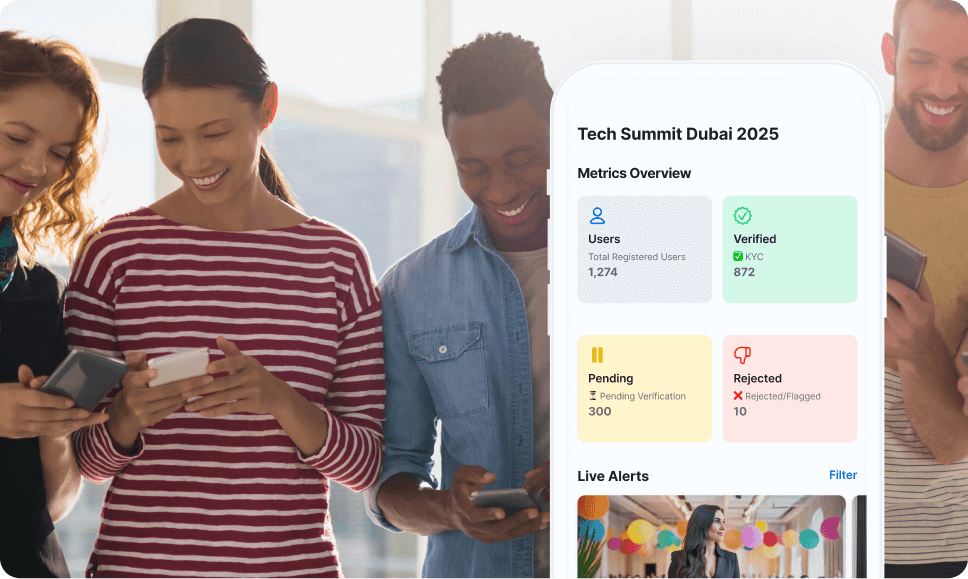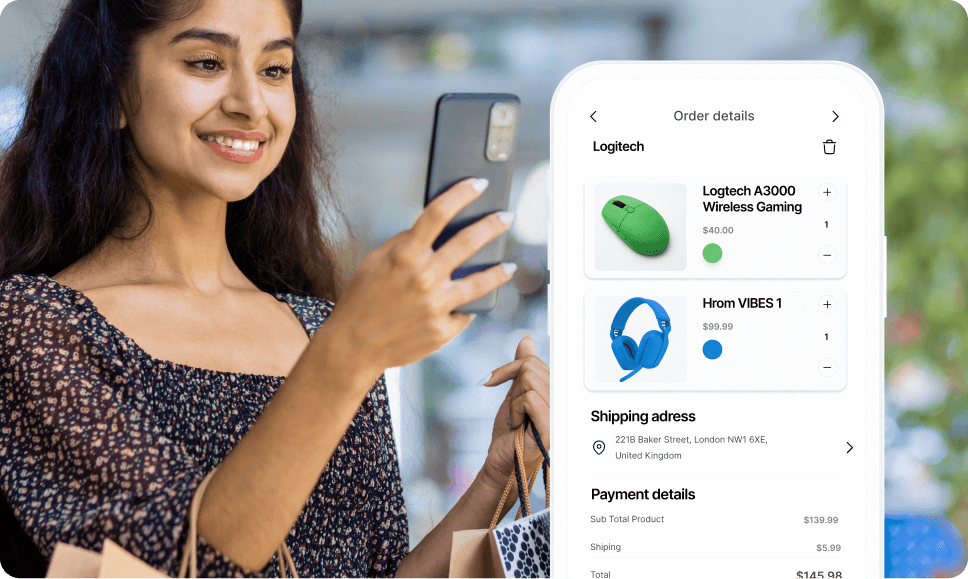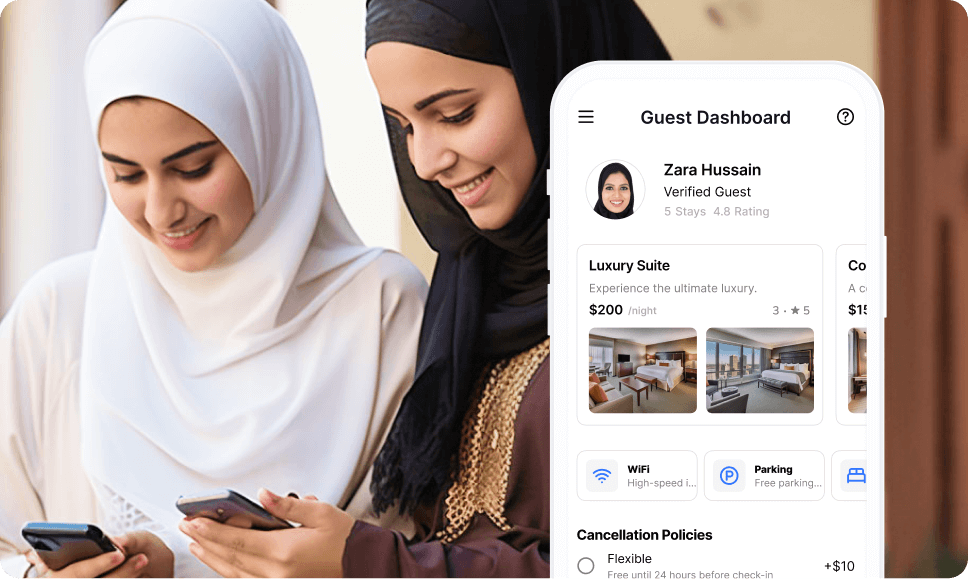
Identity, Fraud & Compliance Solutionsfor Enterprises in MEA
stop fraud before it starts and achieve regulatory compliance.
Our digital identity partners
Comprehensive features across identity
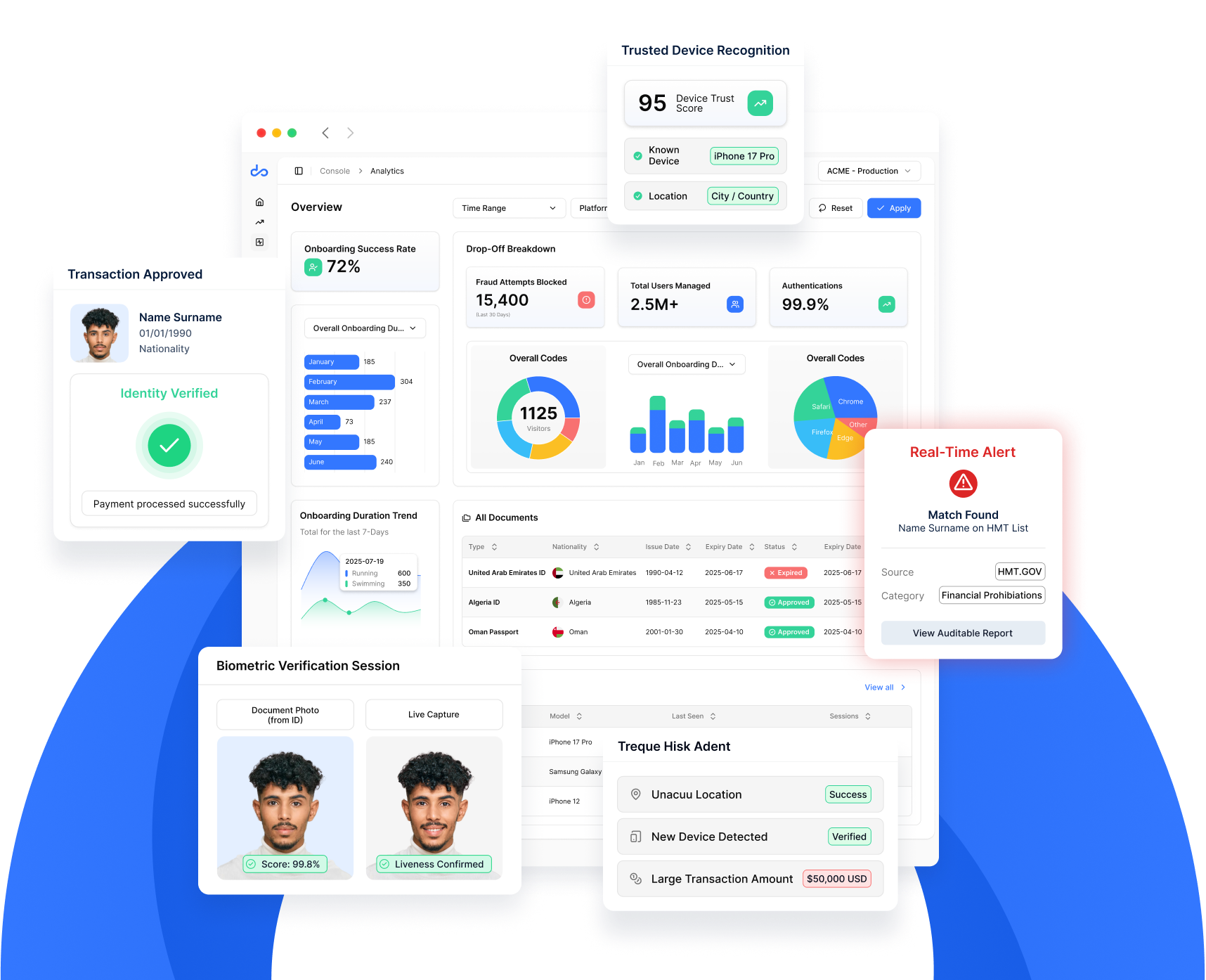
AI Document Scanning
Extract data from Thousands of document types in milliseconds with 99.5% accuracy, enabling frictionless onboarding while preventing document fraud at scale
Multilingual OCR
Process Arabic, Kurdish, and Latin scripts to accurately capture regional identity documents without manual intervention or data entry errors
NFC Chip Reading
Validate 156+ passport types and national ID cards across 22 countries using cryptographic verification that's virtually impossible to forge
National Citizen Registry
Verify individuals directly against government databases in key MEA countries for the highest level of identity assurance possible
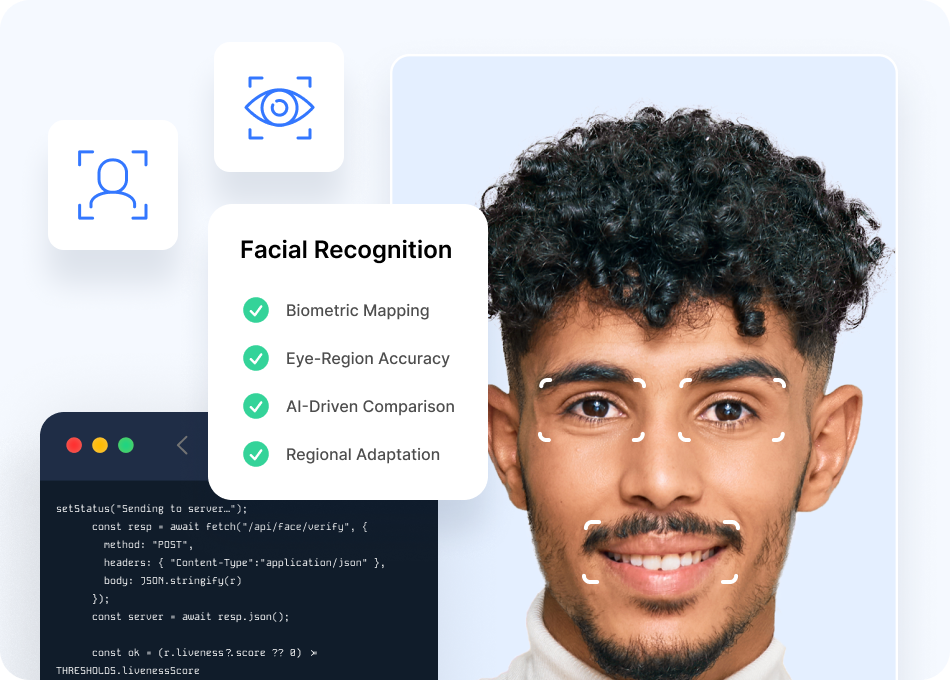
Facial Recognition
Ensure genuine customer presence with biometrics detecting presentation attacks, image injection, and deepfakes
Quality Detection
Assess image quality (lighting, focus, obstruction) to ensure reliable verification while providing clear feedback to users
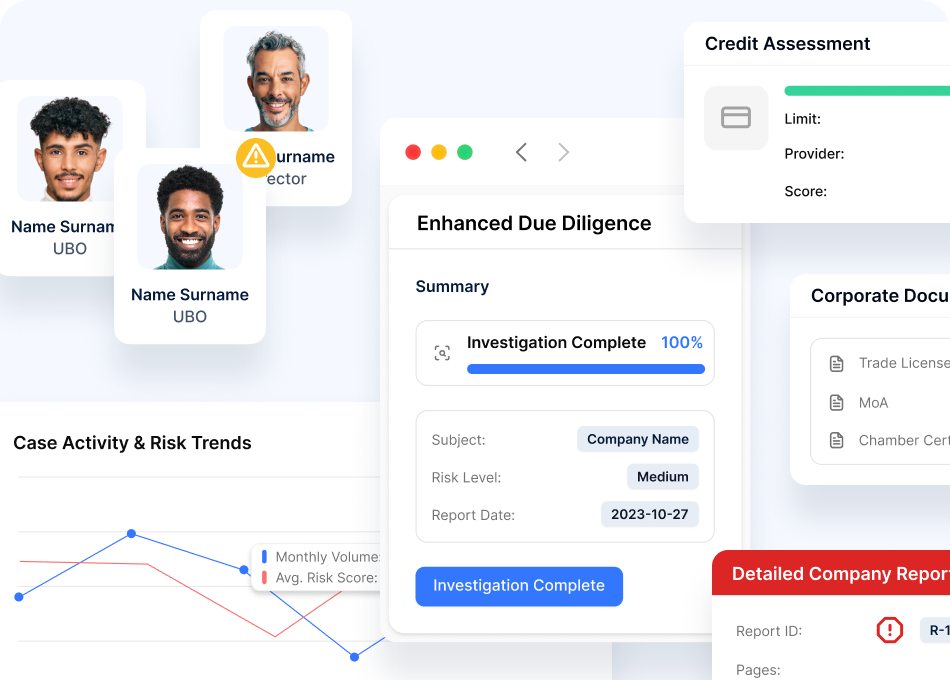
Company Registry Lookup
Access information on 300+ million companies globally through tiered data approach delivering exactly what you need
Automated Document Processing
Validate business documents with AI-powered scanning that extracts and verifies critical information in milliseconds
Director/Shareholder Verification
Verify business principals through automated identity verification integrated with KYC capabilities
Trade License Verification
Validate trade licenses and business registrations with automated OCR and verification
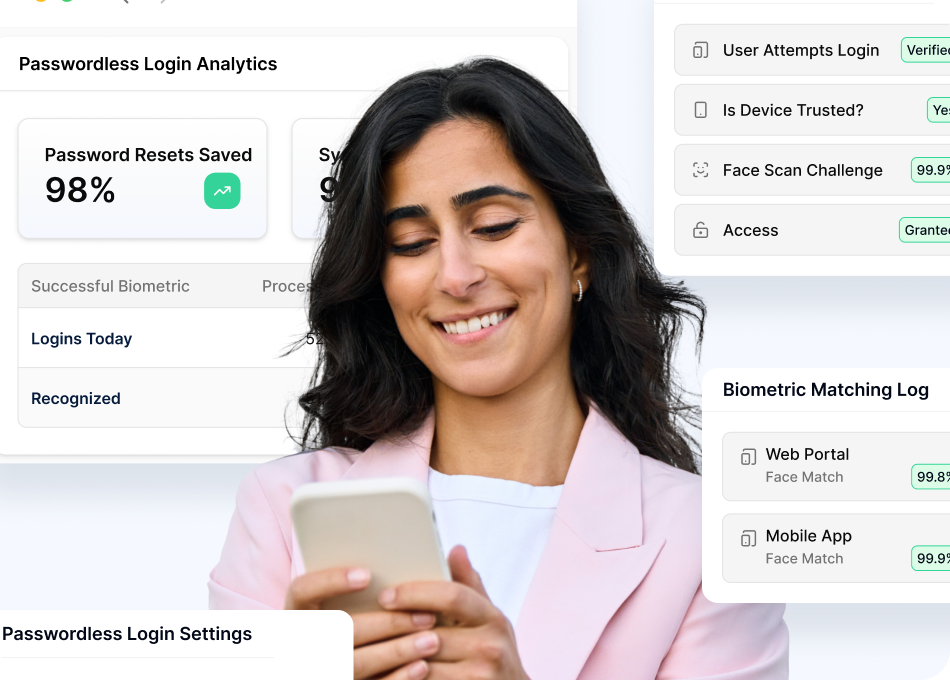
Passwordless Login
Replace passwords with facial recognition to enhance security
Transaction Authorization
Secure high-value operations with biometric verification that prevents unauthorized access while maintaining seamless UX
Account Recovery
Transform password reset into simple biometric verification for instant, secure account restoration
Multi-Factor Authentication
Deploy FIDO2-compliant MFA combining biometrics with device recognition for phishing-resistant security
Continuous Authentication
Verify user identity throughout the session using passive behavioral and contextual signals
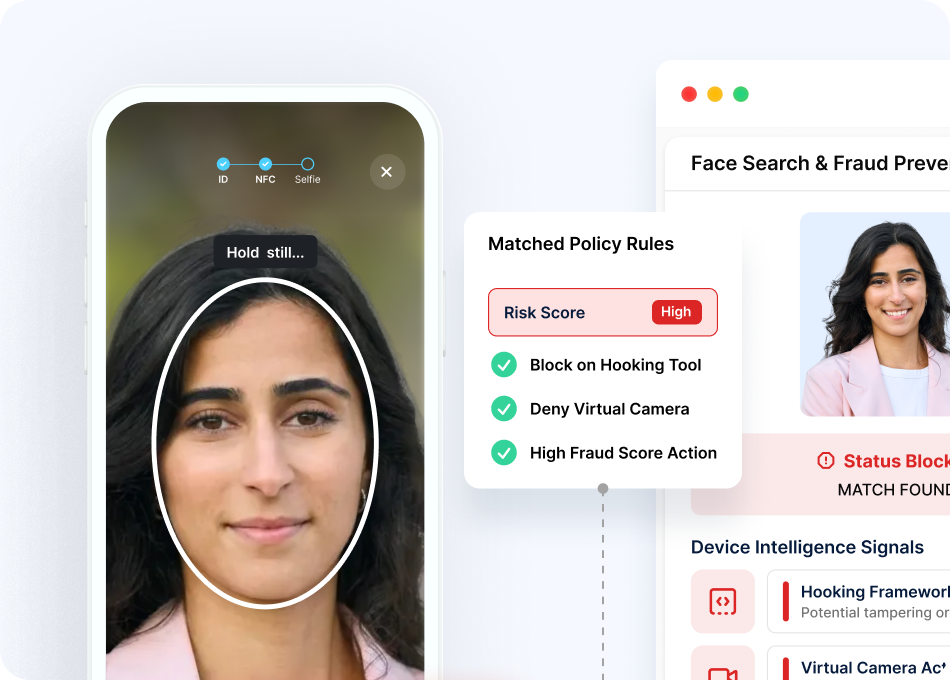
1:N Face Search
Prevent multi-accounting, promo abuse, and fraud rings by matching each user against your entire customer database
Repeat Document Detection
Flag when the same document is used for multiple account attempts stopping bad actors before they succeed

Deepfake Detection
Identify AI-generated or manipulated videos through advanced analysis that distinguishes real humans from synthetic media
Presentation Attack Detection
Prevent photo/video replays, masks, and other presentation attacks through multi-factor liveness analysis
Behavioral Biometrics
Analyze typing patterns, interaction rhythms, and navigation behavior to detect account takeovers and bot activity
Velocity Checks
Monitor account creation rates, transaction frequencies, and other velocity metrics to identify abuse patterns
Bot Detection
Identify automated attacks through interaction pattern analysis, device fingerprinting, and behavioral signals
Account Takeover Prevention
Detect suspicious access attempts through device, location, behavior, and biometric anomalies
Anomaly Detection
Flag unusual patterns in customer behavior, transactions, or account activity for investigation
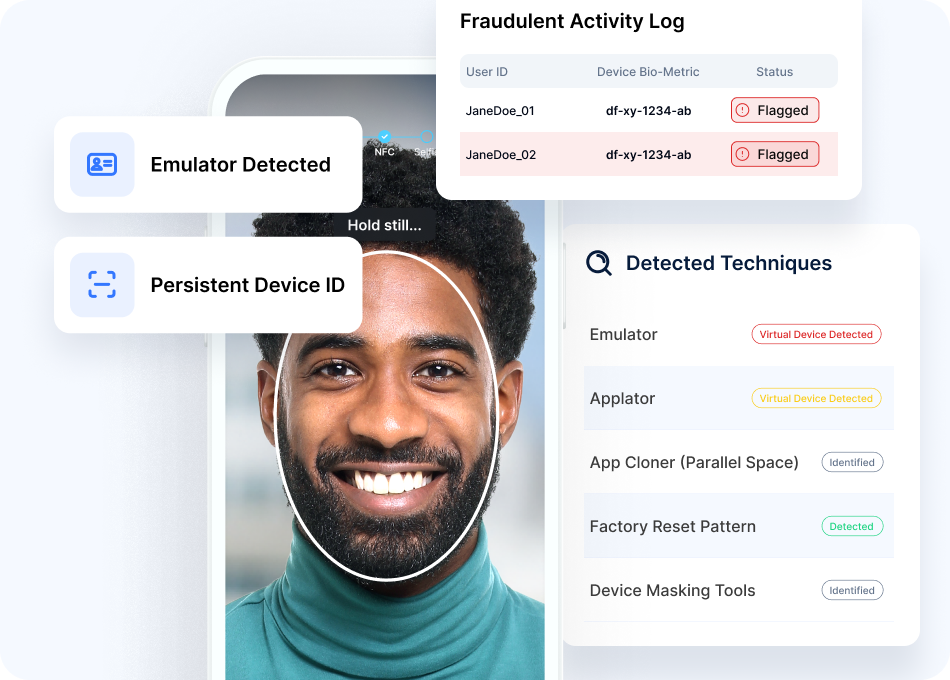
Persistent Device Identification
Persistently identify devices across sessions, reinstalls, factory resets, and OS changes, beyond spoofable IDs like UUIDs and IDFAs with >99.9% accuracy.
App Cloner Detection
Detect app cloners (e.g., Parallel Space, Dual Space) that generate multiple profiles from one device, preventing multi-account fraud and promo abuse at scale.
Emulator Detection
Detect apps running on emulators instead of physical devices, blocking large-scale bot attacks and fraud farms creating thousands of fake accounts.
Device Masking Detection
Expose device identity masking via spoofing tools, modified ROMs, or virtualization, uncovering fraudsters behind fake device profiles.
Jailbreak/Root Detection
Flag rooted or jailbroken devices that disable security controls, preventing privilege escalation and security bypass attacks.
Hooking Detection
Detect hooking tools (e.g., Frida, Xposed) and app tampering used to manipulate verification, inject fake biometrics, or bypass security controls.
GPS Spoofing Detection
Detect GPS spoofing and location manipulation, protecting geo-fencing, location-based services, and compliance checks.
VPN/Proxy Detection
Detect VPN, proxy, or Tor usage that masks true location or network, flagging jurisdiction evasion and regulatory risks.
Suspicious Factory Reset Detection
Flag devices with abnormal factory reset patterns often associated with credential laundering, account cycling, and identity fraud operations
Device Trust Scoring
Real-time risk scoring using 30+ configurable device signals, delivering actionable trust scores with customizable thresholds by use case.
Geolocation Analysis
Assess risk based on device location, IP address, network characteristics, and location history patterns
Continuous Monitoring
Maintain ongoing compliance with automated rescreening that alerts you to changes in customer risk profiles in real-time
Risk Scoring
Assign dynamic risk scores based on screening results, customer profile, and behavioral patterns
Alert Management
Prioritize and investigate AML alerts through purpose-built workflows that streamline compliance operations

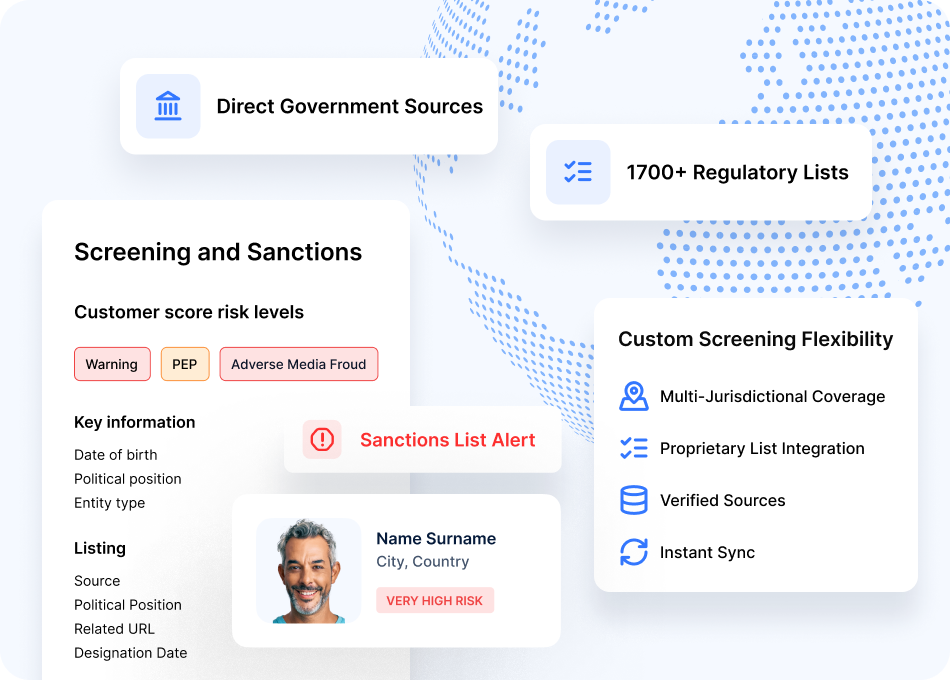
Sanctions Screening
Screen against 1,700+ global sanctions lists with fuzzy name matching to identify sanctioned individuals and entities
PEP Screening
Detect political exposure with access to 1.7+ million PEPs continuously updated by global research analysts
Adverse Media Screening
Protect your brand with advanced monitoring across 3B+ articles from 120,000+ verified global sources.
Entity Resolution
Accurately match entities despite name variations, transliterations, and aliases using advanced fuzzy matching algorithms
Global Watchlist Coverage
Screen against comprehensive databases including OFAC, UN, EU, INTERPOL, and regional watchlists
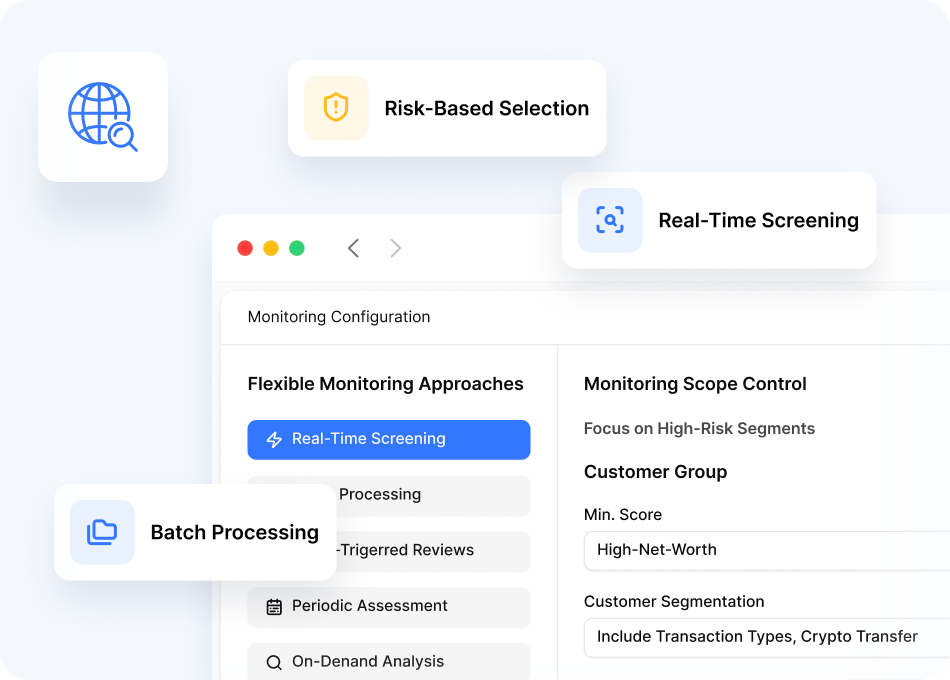
Real-Time Transaction Analysis
Monitor transactions as they occur to detect and prevent fraud before processing completes
Pattern Recognition
Identify suspicious transaction patterns including structuring, round-tripping, and unusual behaviors
No-Code Rule Builder
Create and deploy sophisticated monitoring rules without technical expertise using intuitive visual interface
Case Management
Investigate alerts efficiently with a consolidated view of customer history, relationships, and suspicious activities
SAR/STR Reporting
Automate the generation of Suspicious Activity Reports and Suspicious Transaction Reports for regulatory filing
Velocity & Threshold Monitoring
Track transaction frequencies, amounts, and patterns against configurable thresholds
Cross-Border Transaction Analysis
Apply enhanced scrutiny to international transfers with jurisdiction-specific rules
Anomaly Detection Models
Leverage machine learning to identify deviations from normal customer behavior patterns
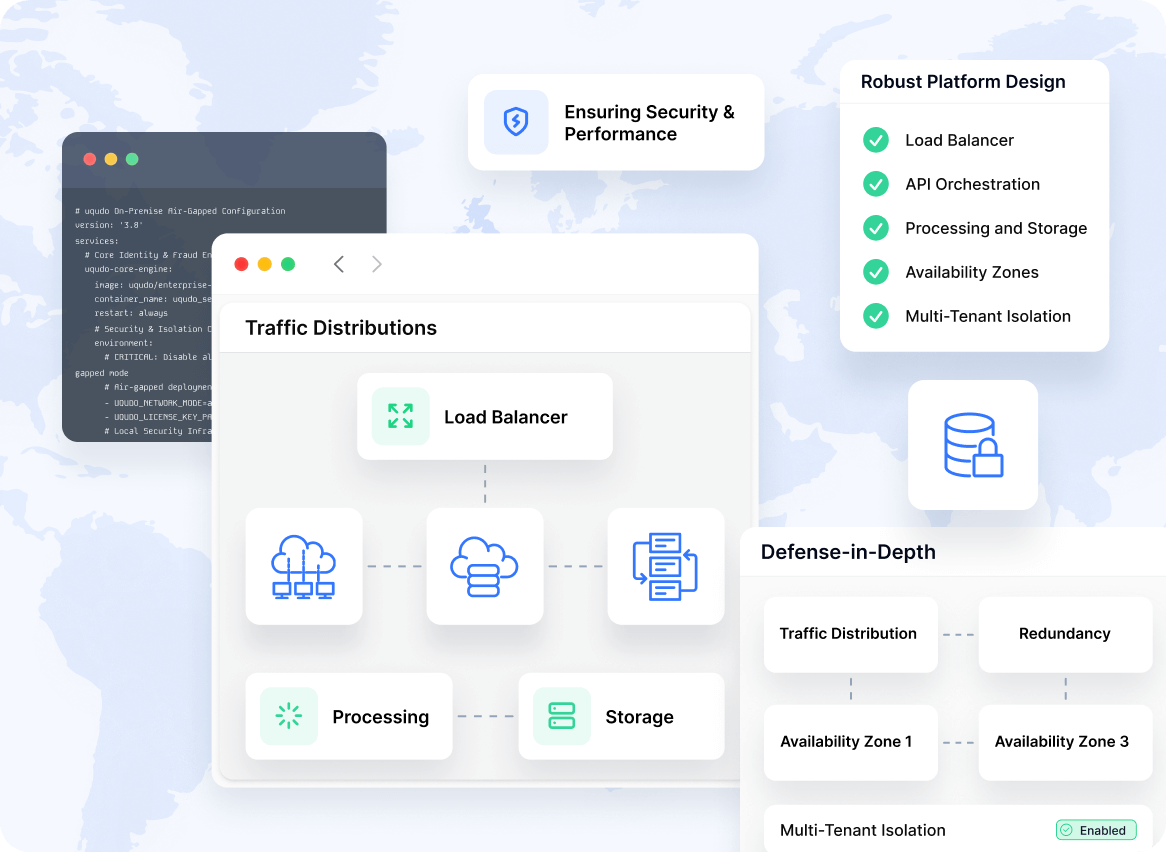
Deploy your way.
Meet MENA data residency requirements

Stay up-to-date with the world of identity
Subscribe to get the latest identity artcles, guides and videos, straight to your email.
We’re committed to your privacy uqudo uses the information you provide to contact you about our content, products, and services. You may unsubscribe from these at any time. For more information, check out our privacy policy.