Table of Contents
- Combatting SIM Swap and Subscription Fraud
- The 30-Second Mandate: Balancing Strict Compliance with User Experience
- Beyond the Selfie: Defeating Deepfakes with Passive Defense
- From “Something You Have” to “Who You Are”: The End of the SMS OTP
- Continuous Authentication: The Invisible Security Layer
- Evaluating Your Current Security Posture: A Practical Framework
The telecommunications sector across the Middle East and Africa stands at a crossroads. On one side, governments are tightening identity verification standards to combat fraud and enhance national security. On the other hand, customer expectations for instant, frictionless service have never been higher. Between these forces, telecom operators face a mounting challenge: how do you secure millions of mobile identities without sacrificing the speed that keeps customers from abandoning sign-up flows?
The answer lies in rethinking mobile identity security not as a compliance checkbox, but as a competitive advantage.
Combatting SIM Swap and Subscription Fraud
SIM swap fraud has emerged as one of the most damaging attack vectors in MEA telecom. Consider a typical scenario: a fraudster calls a customer service center, armed with stolen personal details, and convinces an agent to transfer a victim’s phone number to a new SIM card. Within minutes, they intercept banking OTPs, reset passwords, and drain accounts before the legitimate owner even realizes their number has been hijacked.
These attacks have intensified as digital service adoption accelerates. In Iraq, where the telecom market is projected to reach significant growth over the next decade, the expansion of mobile banking and government digital services has created lucrative new targets for synthetic identity attacks. Fraudsters combine real and fabricated information to create seemingly legitimate profiles that pass basic checks but exist solely to commit fraud. Recent regulatory reforms in Iraq reflect growing awareness of these vulnerabilities, with new identity verification requirements being introduced across the sector.
The technical gap is clear: authentication methods that rely solely on “something you have” (a phone number) fail when that possession can be fraudulently transferred.
The solution requires a shift to biometric identity anchors that cannot be stolen or transferred. Modern facial recognition systems enable telecom operators to compare every new applicant’s face against their entire customer database in real-time, a process known as 1:N face matching. This prevents known fraudsters from creating multiple accounts under different names or re-entering the network after being blacklisted. When combined with behavioral analysis that monitors for unusual patterns during the application process, such as rapid-fire submissions or device spoofing indicators, operators can flag unauthorized number porting attempts before they succeed.
The 30-Second Mandate: Balancing Strict Compliance with User Experience
Across MEA markets, regulatory frameworks have become increasingly stringent, with mandatory SIM registration and comprehensive identity verification requirements becoming standard. For many operators, compliance feels like a burden that adds friction to customer onboarding, leading to higher abandonment rates and lost revenue.
But this perception misses a crucial insight: when implemented correctly, compliance infrastructure can actually accelerate customer acquisition. The key lies in eliminating redundant verification steps and leveraging government data sources directly. Near-field communication technology allows customers to tap their national ID card against their smartphone, instantly extracting and cryptographically validating identity data from the embedded chip. In the UAE, where Emirates ID cards contain NFC chips with biometric and demographic data, this approach achieves the highest level of assurance while dramatically reducing onboarding time.
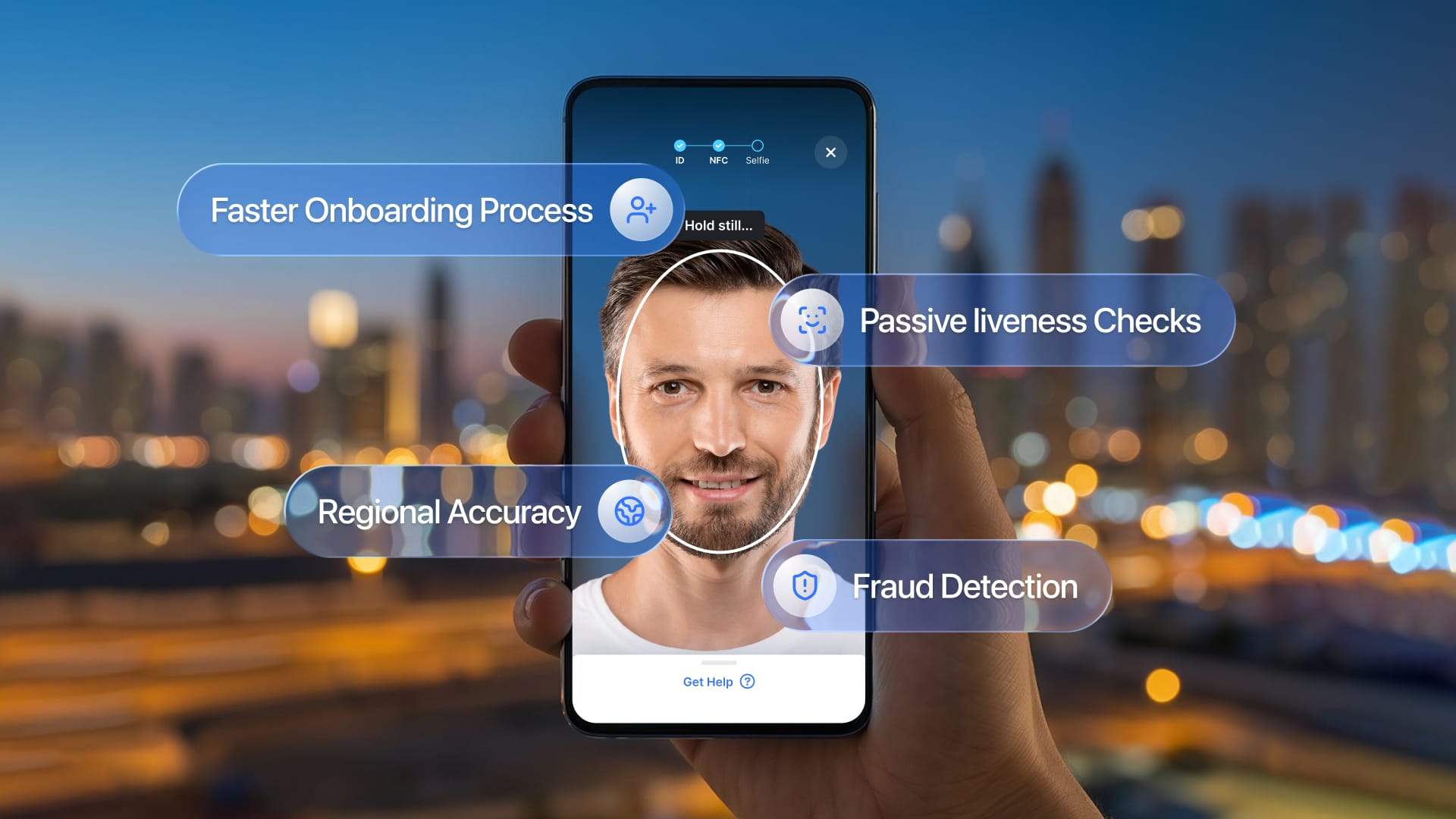
Beyond the Selfie: Defeating Deepfakes with Passive Defense
The rise of generative AI has introduced a new threat: deepfakes sophisticated enough to fool standard facial recognition systems. Fraudsters can now generate synthetic video feeds or use AI-enhanced masks to impersonate legitimate users during video verification. The telecom industry, like banking and government services, finds itself in an escalating arms race.
Traditional “active liveness” checks, which ask users to blink, smile, or turn their heads, add friction to the onboarding experience. Each additional instruction increases the chance that a legitimate customer will abandon the process.
Beyond the user experience cost, active checks also increase processing time and create additional support burden when customers don’t understand the prompts. Moreover, active checks have proven vulnerable to pre-recorded video attacks and 3D-printed masks.
The technical shift underway involves moving toward passive liveness detection and presentation attack detection. These technologies analyze dozens of micro-signals in a single captured image, including:
- Skin texture patterns that reveal the difference between real skin and printed photos or screen displays
- Depth perception cues that detect whether the face is three-dimensional or flat
- Subtle reflections in the eyes and on facial surfaces that distinguish live presence from masks or recordings
Because this analysis happens in the background during a standard selfie capture, users experience no additional friction.
For MEA telecom operators, demographic representation matters significantly. Facial recognition algorithms trained predominantly on Western datasets can produce higher error rates for Middle Eastern and African populations, forcing legitimate customers to retry verification multiple times.
Industry best practices now emphasize training recognition systems on regionally diverse datasets to eliminate this bias and ensure accurate verification across all customer segments without requiring multiple attempts that create frustration and drive abandonment.
From “Something You Have” to “Who You Are”: The End of the SMS OTP
SMS-based two-factor authentication has long been the default security layer for account access and transaction authorization. But beyond its vulnerability to SIM swap attacks, SMS OTP systems carry hidden costs. Telecom operators spend significant amounts annually on SMS delivery fees, particularly for international customers or those roaming. Each failed delivery or delayed message creates support costs and customer dissatisfaction.
The future of mobile identity security lies in FIDO2-compliant biometric authentication. Rather than entering a six-digit code, customers authenticate using their face or fingerprint. This method eliminates both the security weaknesses of SMS and its operational costs. For high-value transactions, such as purchasing premium devices or activating international roaming, biometric authorization provides stronger assurance without adding friction.
In Saudi Arabia, where the biometrics market is experiencing substantial growth driven by government initiatives and private sector adoption, telecom operators have a clear opportunity to lead this transition. Customers increasingly expect the same seamless, secure experiences they encounter in banking apps and government portals. The UAE market provides further evidence of this trend, with mobile wallet adoption projected to reach $8.28 billion by 2030, driven specifically by biometric and contactless payment technologies.
Continuous Authentication: The Invisible Security Layer
While biometric authentication secures the login moment, behavioral biometrics and device fingerprinting create an invisible layer that monitors activity throughout each session, detecting account takeovers even when fraudsters possess valid credentials.
These systems build unique behavioral profiles by analyzing:
- Typing patterns that reveal the unique rhythm and speed of how individuals input text
- Swipe pressure and touch gestures that differ between legitimate users and fraudsters
- Navigation habits showing how users typically move through apps and interfaces
- Device integrity signals such as root detection or emulator usage that indicate compromised environments
When a fraudster attempts to access services using stolen credentials, the behavioral mismatch triggers an alert before damage occurs. Traditional authentication only verifies identity at login; continuous authentication ensures the legitimate user remains in control throughout the entire session.
For telecom operators, this proves particularly valuable for detecting account takeovers that bypass initial authentication, SIM swap attempts from compromised devices, and fraud rings exhibiting similar patterns across multiple accounts. The technology operates invisibly, without disrupting legitimate users.
Evaluating Your Current Security Posture: A Practical Framework
The shared goal across the telecom sector is to reduce customer acquisition costs while preventing fraud from entering the network. High security should not mean high abandonment rates. Yet many operators accept suboptimal conversion rates as inevitable, losing potential customers to unnecessarily complex processes.
Leading operators in the region have demonstrated that strong conversion rates are achievable when identity verification is properly architected. The difference lies in understanding where legitimate customers encounter friction and redesigning those touchpoints.
Assessment Framework for Telecom Operators:
When evaluating identity verification solutions or auditing current systems, consider these critical metrics:
- Document Capture Success Rate: What percentage of customers successfully scan their identity documents on the first attempt?
- Facial Verification Completion Rate: At what stage do customers abandon the facial recognition process?
- Average Onboarding Duration: How long does the complete verification process take from initiation to approval?
- False Rejection Rate: How many legitimate customers are incorrectly flagged and rejected?
- Integration Complexity: How many separate systems must interact to complete verification?
Vendor Selection Criteria:
When evaluating identity verification providers, operators should prioritize:
- Regional Data Training: Confirm that facial recognition and OCR systems have been trained on datasets representing your actual customer demographics, including Arabic and Kurdish script support where relevant.
- Compliance Certification: Ensure solutions meet ISO/IEC 30107-3 standards for presentation attack detection and comply with local data protection regulations.
- Transparent Performance Metrics: Request documented conversion rates, processing times, and false positive/negative rates from existing deployments in similar markets.
- Deployment Flexibility: Assess whether solutions support both cloud-based and on-premise deployment to meet data residency requirements across different jurisdictions.
Operators who enable instant SIM activation, biometric authentication for account recovery, and seamless re-verification build customer loyalty that pricing alone cannot achieve.
The convergence of stricter regulations and sophisticated fraud will make mobile identity security the defining factor separating market leaders from followers across MEA. Operators building this foundation today position themselves to launch mobile financial services, IoT management, and other digital offerings with trusted infrastructure already in place.
Security and experience are no longer opposing forces. Modern biometric authentication, document verification, and fraud prevention technologies prove they reinforce each other. For operators facing conversion or fraud challenges, platforms like uqudo offer KYC, AML screening, and facial recognition solutions purpose-built for MEA markets. Regional leadership comes down to getting architectural choices right from the start.