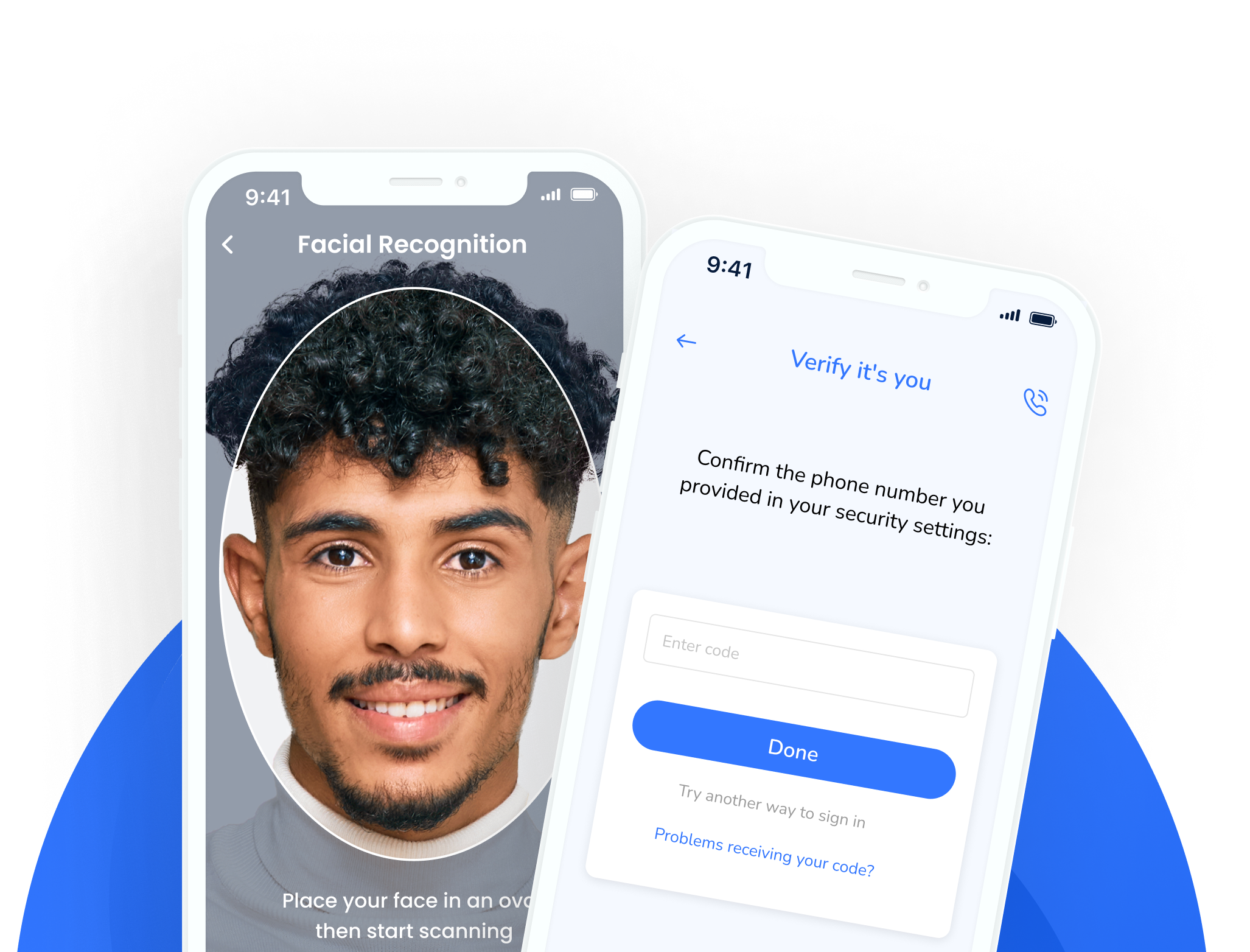
FIDO & FIDO2 Authentication
Use powerful but easier authentication to verify your customer’s identity
Minimise the need of remembering numerous passwords with a more secure authentication method.
See it in action:
Why choose us?
Amplified security
Protect your user data by using unique credentials without using passwords.
Uplift user experience
Provide a streamlined user experience by eliminating passwords.
Easier account recovery
Let your users easily recover their accounts in case of loss of access.
How it works
Step 1
The user chooses a FIDO authenticator to register on the platform.
Step 2
The user then unlocks the FIDO authenticator using a fingerprint, PIN or a second device.
Step 3
The user’s device creates a public/private key, that is unique to the user’s device and account.
Step 4
The public key is stored on the server to associate with the user’s account and the private key never leaves the user’s device.
FIDO & FIDO2 Authentication Features
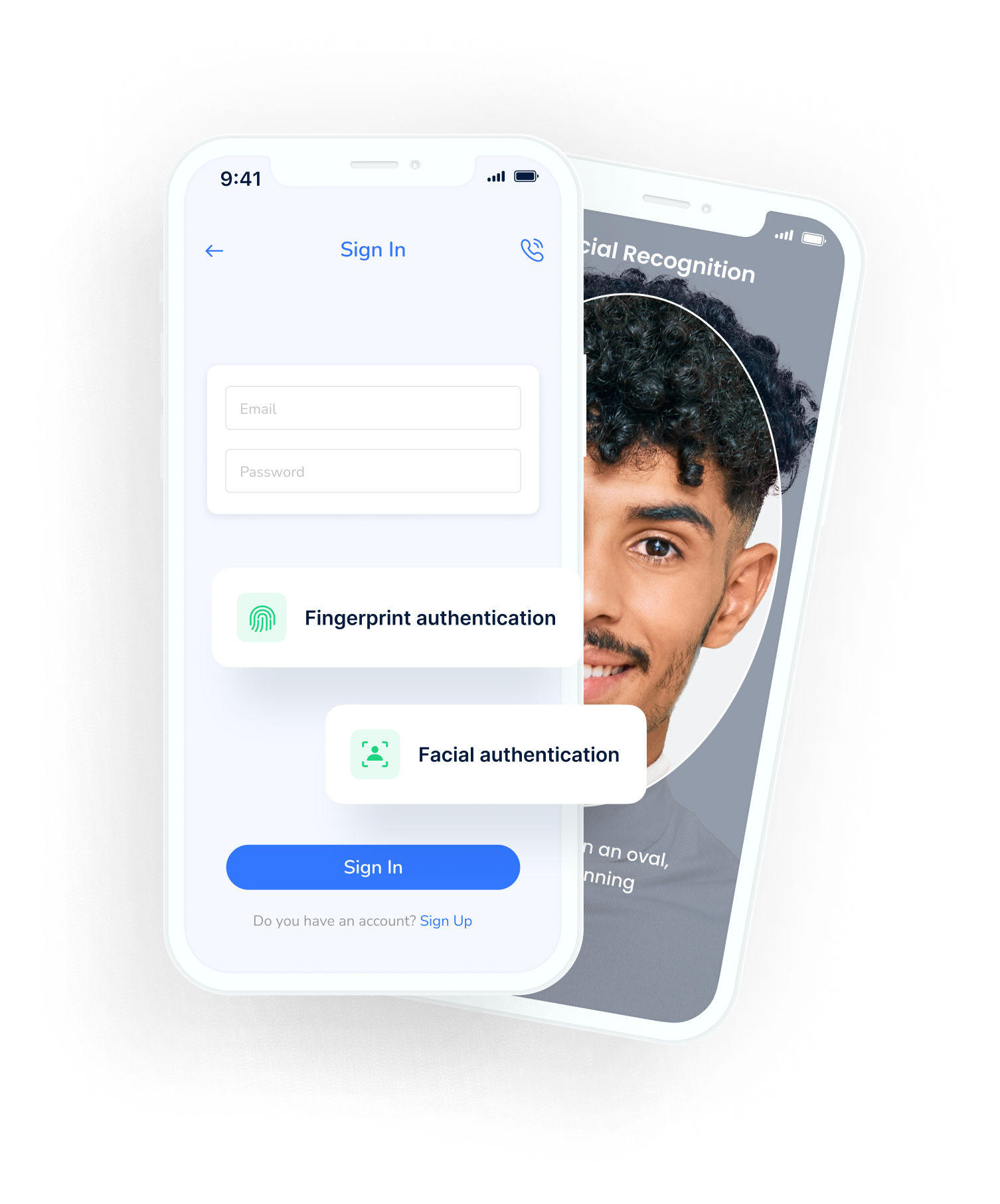
FIDO Passkeys
Use FIDO Authentication credentials digitally sign-up/log in without using passwords.
- Use biometrics (face, fingerprint or voice recognition) or the device’s login PIN to authenticate users.
- Let users log in using different devices in a more secure manner.
More on FIDO and FIDO2 authentication?
The FIDO (Fast IDentity Online) authentication is based on the open standards of the FIDO alliance which aims to reduce the world’s dependence on passwords. Designed to protect users’ privacy and security, FIDO uses private keys and biometrics that never leave the user’s device.
The FIDO protocols use standard public key cryptography techniques to authenticate users.
How does FIDO authentication work?
- While registering a user:
- When a new user is registering with an online service, the user chooses an available authenticator, according to the online services’ policy.
- The user then uses a fingerprint, a second-factor device, a secure PIN or another method to unlock the FIDO authenticator.
- The user’s device creates a new public/private key unique to the user’s device, online service and the user’s account.
- The public key is sent to the online service, associated with the user’s account. The private key remains on the user’s device, which is then used for logging in.
- While registering a user:
- While logging in, the online service asks the user to use the previously registered device.
- The user unlocks the FIDO authenticator, similar to the one done during registration.
- The device uses the online service’s key to identify the user and sign the service’s challenge, which generally includes fingerprint, entering a PIN or pressing a button on the user’s device.
- The user’s device sends the signed challenge back to the online service, which verifies against the public key and lets the user log in.
What is FIDO2?
- The latest FIDO authentication protocol, FIDO2 allows users to easily authenticate themselves, without using passwords, in both mobile and desktop environments. FIDO2 uses the W3C’s Web Authentication (WebAuthn) standard and the Client-to-Authenticator Protocol (CTAP) for passwordless identity verification. Using a combination of cryptography and traditional authentication, FIDO2 helps companies provide secure passwordless access.
Secure, frictionless, & fully compliant digital onboarding. Integrated seamlessly within your app.

Latest Authentication updates
Why is authentication important for your company?
Chandrika Mahapatra
KYC Content Specialist uqudo
How facial recognition is changing digital identity?
Chandrika Mahapatra
KYC Content Specialist uqudo
8 ways OCR enhances digital identity
Chandrika Mahapatra
KYC Content Specialist uqudo
Our clients
Easily integrate  with your tech stack.
with your tech stack.
Use our simple and secure Web SDK, Mobile SDK, or RESTful API to seamlessly integrate identity capabilities into your operations.
See documentationAn award-winning team
uqudo is proud to be recognised by some of the world’s most distinguished organisations.
Here’s what people say about us
-

Abdulmajeed Alsukhan
CEO & Co-Founder Tamara
uqudo, with its user-friendly interface, efficient processes, and responsive team, aligns seamlessly with our dedication to delivering fast, easy, and cost-effective customer authentication experiences. This collaboration fortifies our focus on putting our users first and upholding the highest standards of privacy and security.
-

Xu Chi
VP Ecosystem Cloud Middle East Huawei
Partnering with uqudo will enable Huawei Cloud to offer customers cutting-edge identity verification, contributing to the goal of building a more secure and inclusive digital world.
-

Joseph Dallago
CEO Rain Crypto
We are thrilled to partner with uqudo to leverage their innovative and secure identity technology into our customer’s onboarding process. By prioritising security and user-friendliness, we aim to make the benefits and opportunities provided by cryptocurrencies more accessible to individuals in the region.
-

Maqbool Al Wahaibi
CEO Oman Data Park
Oman Data Park is committed to providing our customers with the latest and most advanced technology solutions. Our partnership with uqudo will help us to further enhance our services and deliver fraud-proof digital identity solutions to our customers in Oman.
-

Jude Dike
CEO Get Equity
After our research, we found uqudo to be by far the best AML provider and we are confident that they will help us push our business forward as we grow.
-

Mehdi Fichtali
Founder & CEO FinaMaze
What made us choose Uqudo as our digital identity partner is their clear and fast integration process and the constant availability and efficiency of their support team. The client ID verification and video selfie is user-friendly and convenient making our onboarding process quasi-instant.
We price based on successful onboarding.
Say goodbye to request-based fees, repeat charges, and spiralling customer acquisition costs.
FAQ
What is Biometric Authentication?
Every individual is unique and through the use of biometrics, we can use aspects of uniqueness to authenticate a person’s identity. Everything from the face, fingerprint, palm, and voice can be used to verify a person is who they say they are. Given most ID documents are photo IDs, the face is the most common and popular way to authenticate with biometrics.
How can biometric authentication help my company?
Biometric authentication provides the opportunity for passwordless logins for your users. Logging in with the face is both faster and more secure. Strong authentication refers to the set of specifications laid out by FIDO. These specifications mean authentication is intrinsically stringent enough to ensure the security of the system it protects.
Is facial recognition safe?
Biometric face authentication uses unique facial patterns to identify people, making it highly efficient. Since our platform doesn’t store data, all biometric information is encrypted and secure.
What all biometric authentication methods can be used?
uqudo lets your customers use the following biometrics for authentication:
- Face
- Fingerprint
- Voice
- Iris
- Palm
How does 2FA work?
Our two-factor authentication (2FA) uses facial biometrics as the second factor to provide a non-invasive second layer of authentication, to keep your customer data secure.
Which documents do you support?
uqudo’s AI Document Scanning can read and extract identity data from 98% of commonly used identity documents in EMEA. Check out our Coverage & Capabilities for a full breakdown of supported documents filtered by geography.
Which documents can you verify?
We are able to read all passports with an NFC chip and verify passports in 86 countries. In addition to this, we are able to verify identity cards in a total of 11 countries currently. For a full list of the documents that we are able to verify visit our Coverage & Capabilities page.
















 with your tech stack.
with your tech stack.














