Table of Contents
- Protecting What Matters: The Urgent Need for Stronger Digital Security
- Unlocking Superior Security: How Two-Factor Authentication Works
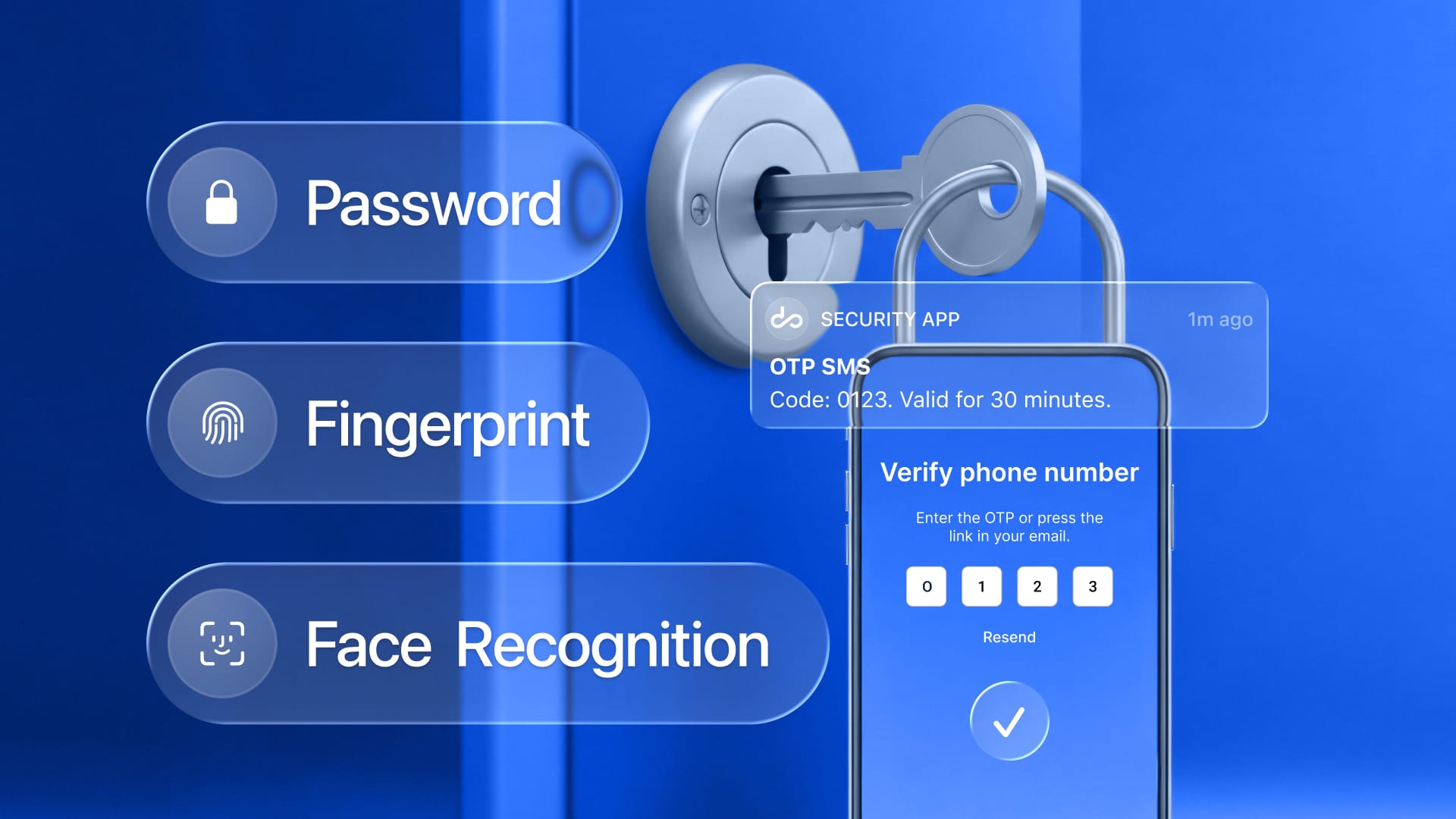
- Your Arsenal of Defense: A Look at 2FA Methods
- The Real Impact: Why 2FA is Non-Negotiable for Your Digital Life
- Making It Happen: A Practical Guide to Implementing 2FA
- Your Digital Shield: A Final Call to Embrace 2FA
Protecting What Matters: The Urgent Need for Stronger Digital Security
Passwords alone no longer protect your digital identity. Whether through data breaches exposing millions of credentials or sophisticated phishing campaigns, cybercriminals have rendered single-factor authentication obsolete. The gap between traditional security and modern threats widens daily, leaving individuals and organizations dangerously exposed. Yet the solution, adding just one additional layer of verification, can block nearly all unauthorized access attempts.
Unlocking Superior Security: How Two-Factor Authentication Works
Two-factor authentication (2FA) transforms the security landscape by requiring users to provide two distinct forms of identification before accessing their accounts. This approach operates on a fundamental principle: combining something you know (like a password) with something you have (like a smartphone) or something you are (like a fingerprint).
The mechanics are elegantly simple yet remarkably effective. When you attempt to log into a 2FA-protected account, the system first verifies your password. Upon successful password entry, it then requests a second form of verification. This could be a unique code sent to your registered mobile device, a biometric scan, or a response from a dedicated authentication app. Only when both factors are successfully verified does the system grant access.
This dual-layer approach creates a formidable barrier against unauthorized access. Even if cybercriminals obtain your password through a data breach or phishing attack, they cannot access your account without the second authentication factor.
The beauty of 2FA lies in its adaptability. Organizations can implement various combinations of authentication factors based on their security requirements and user preferences, ensuring both robust protection and user convenience.
Your Arsenal of Defense: A Look at 2FA Methods
Modern 2FA implementation offers diverse methods, each with unique advantages tailored to different security needs and user preferences.
Authenticator Applications generate time-sensitive codes on your device, eliminating the need for cellular networks. These apps work offline and can secure multiple accounts from a single interface. They offer enhanced security over SMS while maintaining ease of use.
Biometric Authentication leverages unique physical characteristics like fingerprints, facial recognition, or voice patterns. This method offers unparalleled convenience since users cannot forget or lose their biometric identifiers. Advanced biometric authentication solutions incorporate liveness detection to prevent spoofing attempts using photos or recordings.
Hardware Security Keys provide the highest level of security through physical devices that must be present during authentication. These keys are virtually impossible to phish remotely and ideal for protecting high-value accounts.
Push Notifications streamline authentication by sending approval requests directly to registered devices. Users simply approve or deny access attempts with a single tap, combining strong security with minimal friction.
SMS-based authentication remains the most widely adopted method, sending one-time codes via text message to registered phone numbers. While convenient and requiring no additional apps, SMS authentication faces vulnerabilities from SIM swapping attacks, where criminals hijack phone numbers to intercept codes.
The Real Impact: Why 2FA is Non-Negotiable for Your Digital Life
The implementation of 2-factor authentication solutions delivers transformative benefits across personal and professional contexts. For individuals, it creates a robust shield around digital assets, protecting everything from financial accounts to personal photos and private communications. The peace of mind from knowing your accounts have multiple layers of protection cannot be overstated.
In the business realm, 2FA serves as a critical component of comprehensive security strategies. Organizations implementing robust authentication see dramatic reductions in account takeover incidents, data breaches, and associated costs. This protection extends beyond direct financial losses to preserve customer trust and corporate reputation.
2FA also facilitates compliance with evolving data protection standards. As regulatory frameworks increasingly mandate strong authentication for accessing sensitive systems, organizations with established 2FA protocols find themselves ahead of compliance curves. This proactive approach to security can differentiate businesses in competitive markets where customers increasingly value data protection.
The technology sector has embraced 2FA as standard practice, recognizing that traditional passwords alone cannot protect against modern threats. Financial services and government agencies follow suit, making 2FA a baseline expectation rather than an optional enhancement.
With the benefits clear and the risks undeniable, the question becomes not whether to implement 2FA, but how to begin.
Making It Happen: A Practical Guide to Implementing 2FA
Strategic Planning for Customer-Facing 2FA
Businesses implementing 2FA for their customers must balance security requirements with user experience. Start by mapping customer journeys to identify authentication touchpoints where additional verification adds value without creating friction. High-value transactions, account changes, and first-time device access typically warrant stronger authentication, while routine activities maintain simpler flows.
Building Your 2FA Infrastructure
Organizations face critical decisions about deployment architecture. Cloud-based identity platforms enable rapid implementation with built-in scalability, while on-premise solutions offer complete data control for regulated industries. Hybrid approaches combine cloud flexibility with local data storage, meeting compliance requirements without sacrificing performance.
Integration requires careful API design to minimize disruption to existing systems. Authentication services should operate as independent microservices, communicating through secure protocols with your core applications. This modular approach enables updates without affecting primary business logic while supporting gradual feature rollouts.
Customer data flow must remain secure throughout the authentication process. Implement end-to-end encryption for all verification channels, tokenize sensitive information, and establish clear data retention policies. Regular security audits ensure these protections remain effective as your implementation scales.
Choosing Authentication Methods for Your Customers
Modern 2FA offers diverse verification options beyond traditional SMS codes. Biometric authentication leverages unique physical characteristics like fingerprints, facial recognition, or voice patterns — voice biometric authentication solutions, for example, analyze and verify users based on their unique vocal traits. These methods offer unparalleled convenience, since customers cannot forget or lose their biometric identifiers. Push notifications streamline authentication by sending approval requests directly to registered devices, where users simply approve or deny access attempts with a single tap.
Authenticator applications generate time-sensitive codes on customer devices, eliminating the need for cellular networks while working offline and securing multiple accounts from a single interface. Hardware security keys provide the highest level of security through physical devices that must be present during authentication, making them virtually impossible to phish remotely and ideal for protecting high-value accounts. Each method carries distinct implementation requirements and user experience implications that shape adoption success.
Managing the Customer Experience
Successful 2FA implementation prioritizes user experience alongside security. Clear setup communication and interactive tutorials build trust while reducing support contacts. Robust account recovery requires multiple paths including backup codes and alternative verification methods, balancing security with accessibility.
Error handling demands specific guidance rather than generic messages. Distinguish between incorrect codes, expired tokens, and system issues to help customers resolve problems quickly. Progressive retry limits prevent attacks while accommodating legitimate users.
As customer expectations and authentication technologies evolve, businesses must adapt their 2FA strategies through continuous monitoring of metrics, feedback, and security incidents. By treating implementation as an ongoing journey, organizations create authentication experiences that protect accounts while enhancing digital interactions.
Your Digital Shield: A Final Call to Embrace 2FA
We’ve explored the vulnerabilities of password-only security, understood how 2FA creates multiple defensive layers, and examined implementation methods. The evidence is overwhelming: Two-factor authentication isn’t just another security feature; it’s your essential shield against escalating cyber threats.
Every unprotected account represents a potential domino in a chain of compromises. Whether safeguarding personal data or protecting customer trust, the minimal effort required to enable 2FA pales against the devastating consequences of identity theft or data breaches.
As businesses worldwide recognize this imperative, identity verification platforms are making enterprise-grade security accessible to organizations of all sizes. At uqudo we have pioneered solutions that integrate Two-Factor Authentication with advanced Biometric Authentication, enabling businesses to deploy robust security that enhances user experience across sectors such as Banking, Crypto Exchanges, and Digital Commerce. Their work across diverse sectors demonstrates that security excellence and business growth go hand in hand.
Don’t wait for a breach to convince you. Enable 2FA on every available account today. Your digital identity and your future self will thank you for taking this crucial step.