Two-Factor Authentication
Secure your digital platform with two-factor authentication
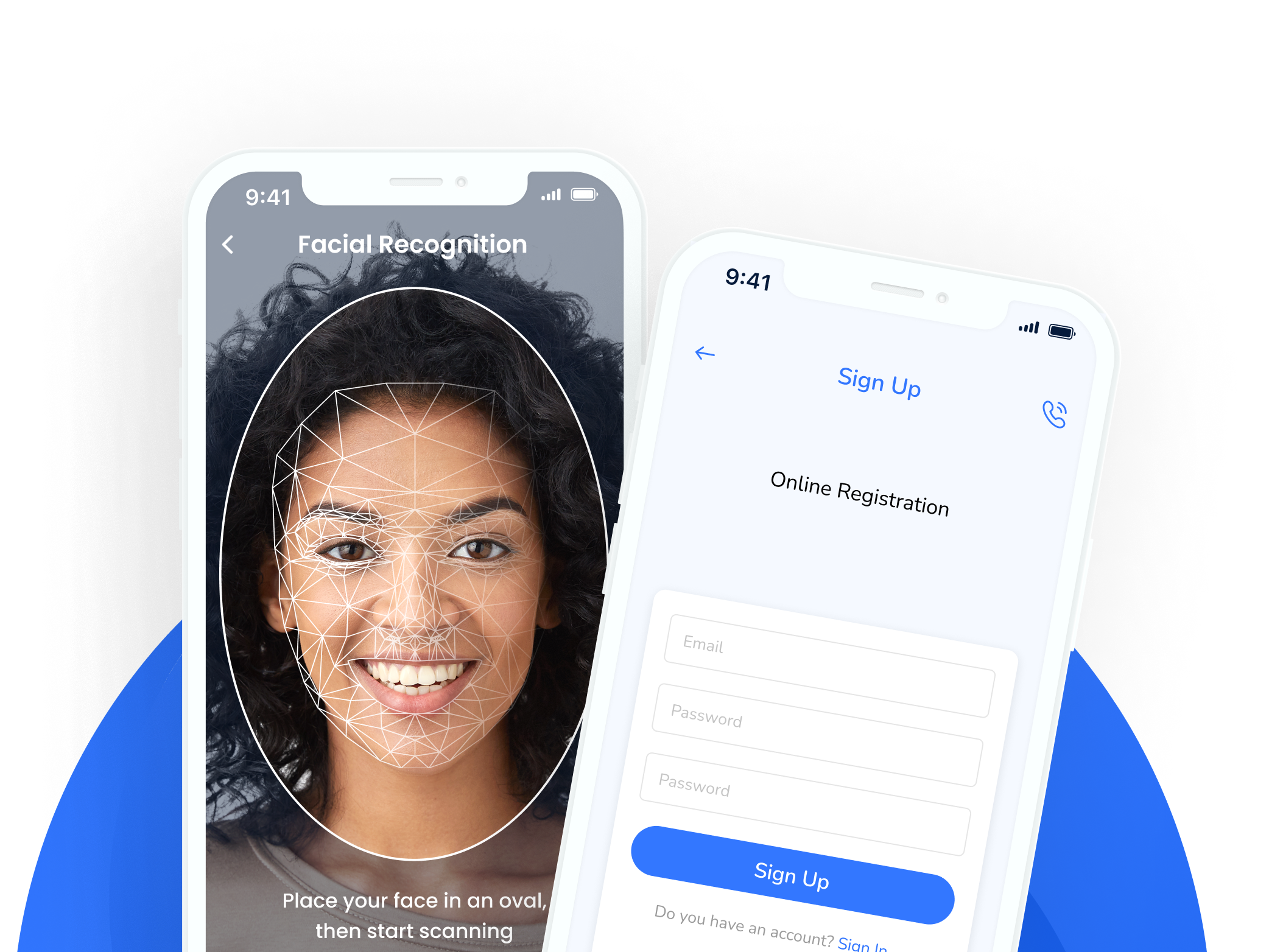
Double-up security and prevent unauthorised access using two authentication methods to validate your users’ identities.
See it in action:
Why choose us?
Greater protection
Add an extra layer of security, reducing the possibility of unauthorised access.
Enhance customer trust
Increase your users’ faith in the security of their personal data with multiple authentication factors.
Reduce password fatigue
Enable your users to remember a lesser number of passwords with an easier 2FA.
Reduce operating costs
Save money by keeping your users aware of suspicious activities, reducing fraud.
How it works?
Step 1
User enrols into the system using a username and password.
Step 2
User provides facial biometrics as the second authentication while onboarding.
Step 3
While logging in, the user inputs a password, after which facial verification is done.
Two-Factor Authentication Features
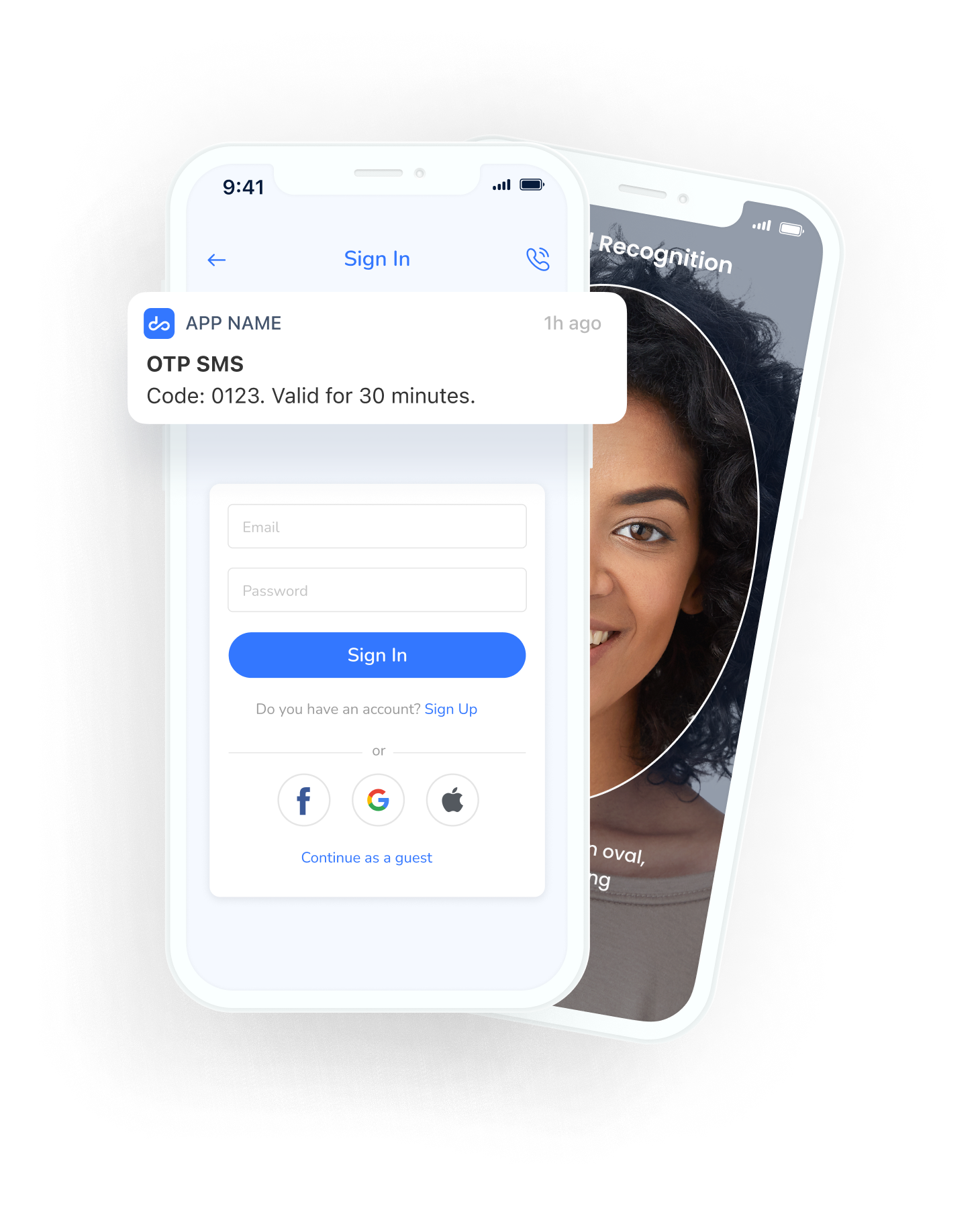
Use a combination of different authentication methods to double up your users’ security:
- Biometrics
- Push notifications
- SMS OTPs (One-Time Passwords)
- FIDO universal factor
- Software tokens
- Hardware tokens
More on two-factor authentication
With passwords being increasingly vulnerable, organisations today have understood the necessity of stronger authentication methods. A type of multi-factor authentication, 2FA provides an extra layer of security to users trying to gain access to their online accounts. Since 2FA generally involves a combination of passwords and authentication done on the user’s physical device, it makes it difficult for cybercriminals to gain access to sensitive information.
Authentication methods used in 2FA are generally a combination of:
- Something the user knows: This refers to a password, a PIN or an answer to a secret security question.
- Something the user is: Also called the inherent factor, this refers to the biometric information of the user, including fingerprints, facial features, voice, retina, or iris.
- Something the user has: This includes a specific piece of information or a device a user has. Examples of possession factors include an OTP (One-Time Password) or a code sent to the user’s email account.
The reason two-factor authentication methods are common today is that even if a user’s password credentials are compromised, it is very difficult for a hacker to validate themselves without possessing the user’s physical device. This in turn helps companies keep their customer data secure, and verify identities more confidently.
Secure, frictionless, & fully compliant digital onboarding. Integrated seamlessly within your app.

Latest Authentication updates
Why is authentication important for your company?
Chandrika Mahapatra
KYC Content Specialist uqudo
How facial recognition is changing digital identity?
Chandrika Mahapatra
KYC Content Specialist uqudo
8 ways OCR enhances digital identity
Chandrika Mahapatra
KYC Content Specialist uqudo
Our clients
Easily integrate  with your tech stack.
with your tech stack.
Use our simple and secure Web SDK, Mobile SDK, or RESTful API to seamlessly integrate identity capabilities into your operations.
See documentationAn award-winning team
uqudo is proud to be recognised by some of the world’s most distinguished organisations.
Here’s what people say about us
-

Abdulmajeed Alsukhan
CEO & Co-Founder Tamara
uqudo, with its user-friendly interface, efficient processes, and responsive team, aligns seamlessly with our dedication to delivering fast, easy, and cost-effective customer authentication experiences. This collaboration fortifies our focus on putting our users first and upholding the highest standards of privacy and security.
-

Xu Chi
VP Ecosystem Cloud Middle East Huawei
Partnering with uqudo will enable Huawei Cloud to offer customers cutting-edge identity verification, contributing to the goal of building a more secure and inclusive digital world.
-

Joseph Dallago
CEO Rain Crypto
We are thrilled to partner with uqudo to leverage their innovative and secure identity technology into our customer’s onboarding process. By prioritising security and user-friendliness, we aim to make the benefits and opportunities provided by cryptocurrencies more accessible to individuals in the region.
-

Maqbool Al Wahaibi
CEO Oman Data Park
Oman Data Park is committed to providing our customers with the latest and most advanced technology solutions. Our partnership with uqudo will help us to further enhance our services and deliver fraud-proof digital identity solutions to our customers in Oman.
-

Jude Dike
CEO Get Equity
After our research, we found uqudo to be by far the best AML provider and we are confident that they will help us push our business forward as we grow.
-

Mehdi Fichtali
Founder & CEO FinaMaze
What made us choose Uqudo as our digital identity partner is their clear and fast integration process and the constant availability and efficiency of their support team. The client ID verification and video selfie is user-friendly and convenient making our onboarding process quasi-instant.
We price based on successful onboarding.
Say goodbye to request-based fees, repeat charges, and spiralling customer acquisition costs.
FAQ
What is Biometric Authentication?
Every individual is unique and through the use of biometrics, we can use aspects of uniqueness to authenticate a person’s identity. Everything from the face, fingerprint, palm, and voice can be used to verify a person is who they say they are. Given most ID documents are photo IDs, the face is the most common and popular way to authenticate with biometrics.
How can biometric authentication help my company?
Biometric authentication provides the opportunity for passwordless logins for your users. Logging in with the face is both faster and more secure. Strong authentication refers to the set of specifications laid out by FIDO. These specifications mean authentication is intrinsically stringent enough to ensure the security of the system it protects.
Is facial recognition safe?
Biometric face authentication uses unique facial patterns to identify people, making it highly efficient. Since our platform doesn’t store data, all biometric information is encrypted and secure.
What all biometric authentication methods can be used?
uqudo lets your customers use the following biometrics for authentication:
- Face
- Fingerprint
- Voice
- Iris
- Palm
How does 2FA work?
Our two-factor authentication (2FA) uses facial biometrics as the second factor to provide a non-invasive second layer of authentication, to keep your customer data secure.
Which documents do you support?
uqudo’s AI Document Scanning can read and extract identity data from 98% of commonly used identity documents in EMEA. Check out our Coverage & Capabilities for a full breakdown of supported documents filtered by geography.
Which documents can you verify?
We are able to read all passports with an NFC chip and verify passports in 86 countries. In addition to this, we are able to verify identity cards in a total of 11 countries currently. For a full list of the documents that we are able to verify visit our Coverage & Capabilities page.
Privacy Overview
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-advertisement | 1 year | Advertisement cookies are used to provide visitors with relevant ads and marketing campaigns. These cookies track visitors across websites and collect information to provide customized ads. |
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |

Please wait while you are redirected to the right page...
















 with your tech stack.
with your tech stack.














