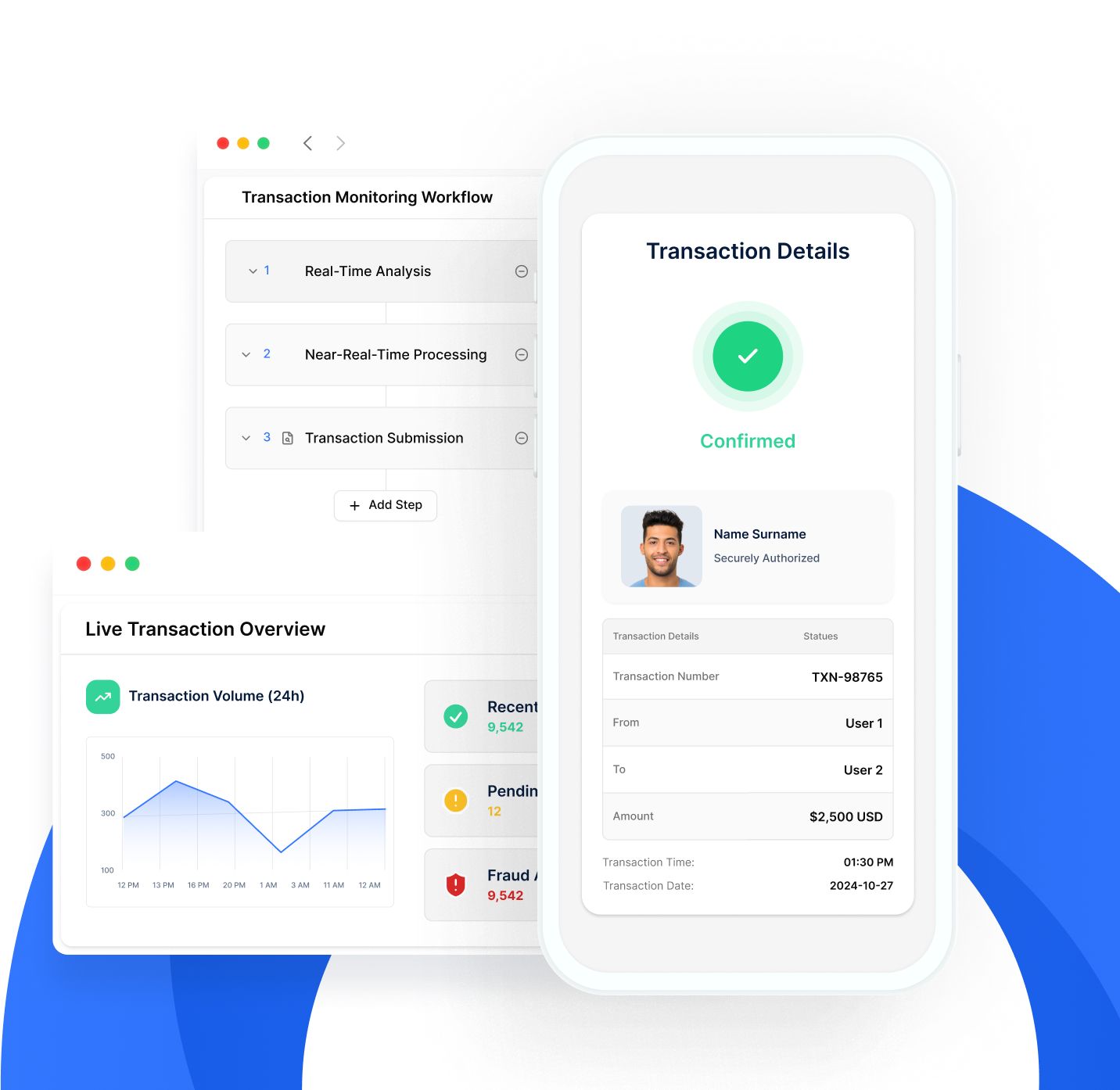
Transaction Authorization
Secure Verification for High-Value Actions
uqudo’s Transaction Authorization solution provides robust verification for sensitive operations while maintaining a seamless user experience.
Key Capabilities
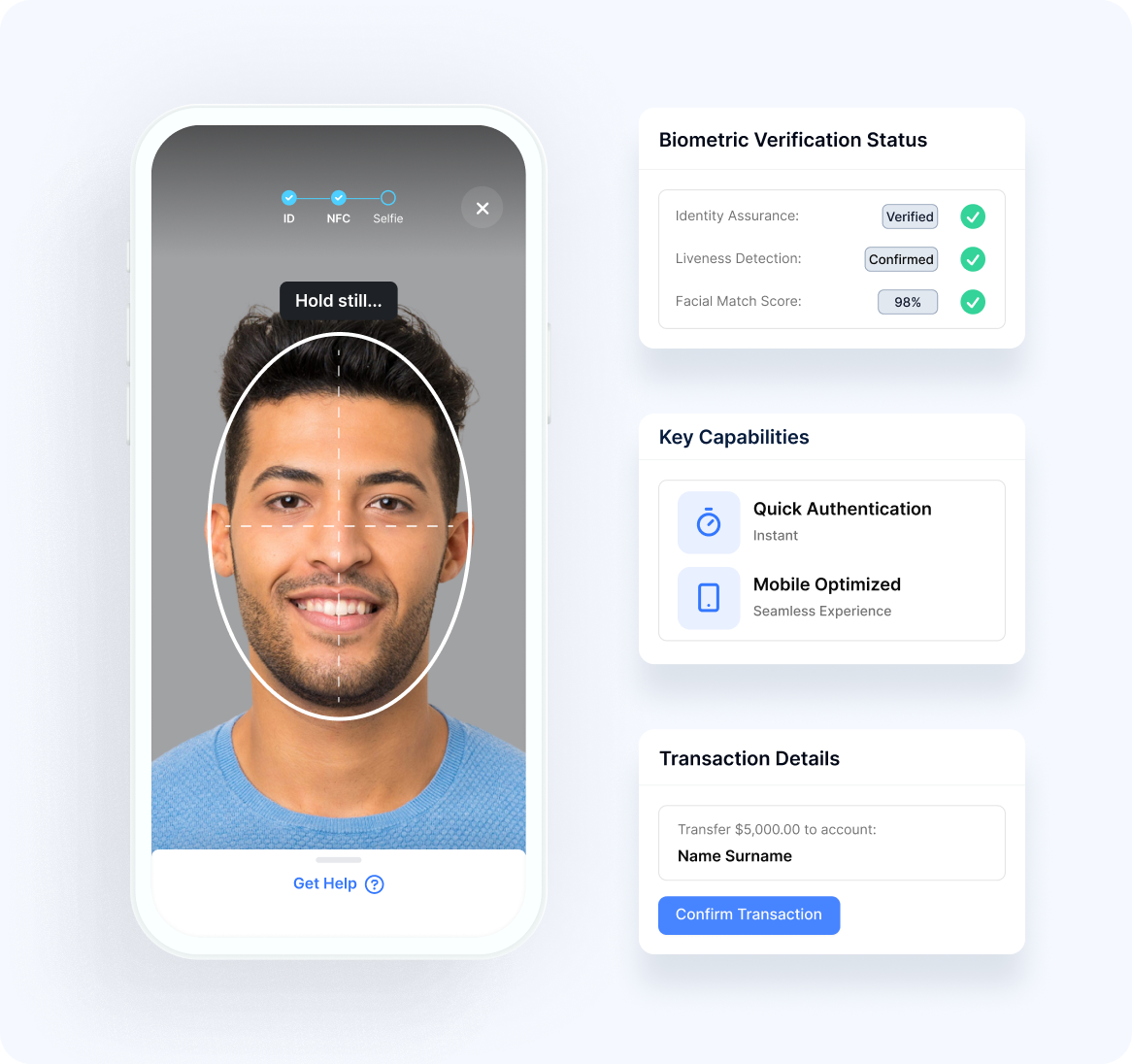
Biometric Transaction Verification
Our platform employs facial recognition for secure action confirmation:
Biometric Authorization
- Identity AssuranceVerification of the user’s identity for critical transactions
- Liveness DetectionConfirmation of genuine user presence during authorization
- Intent ConfirmationExplicit verification of the user’s desire to proceed
- Quick AuthenticationRapid verification to maintain transaction flow
- Mobile OptimizationStreamlined experience on smartphones and tablets
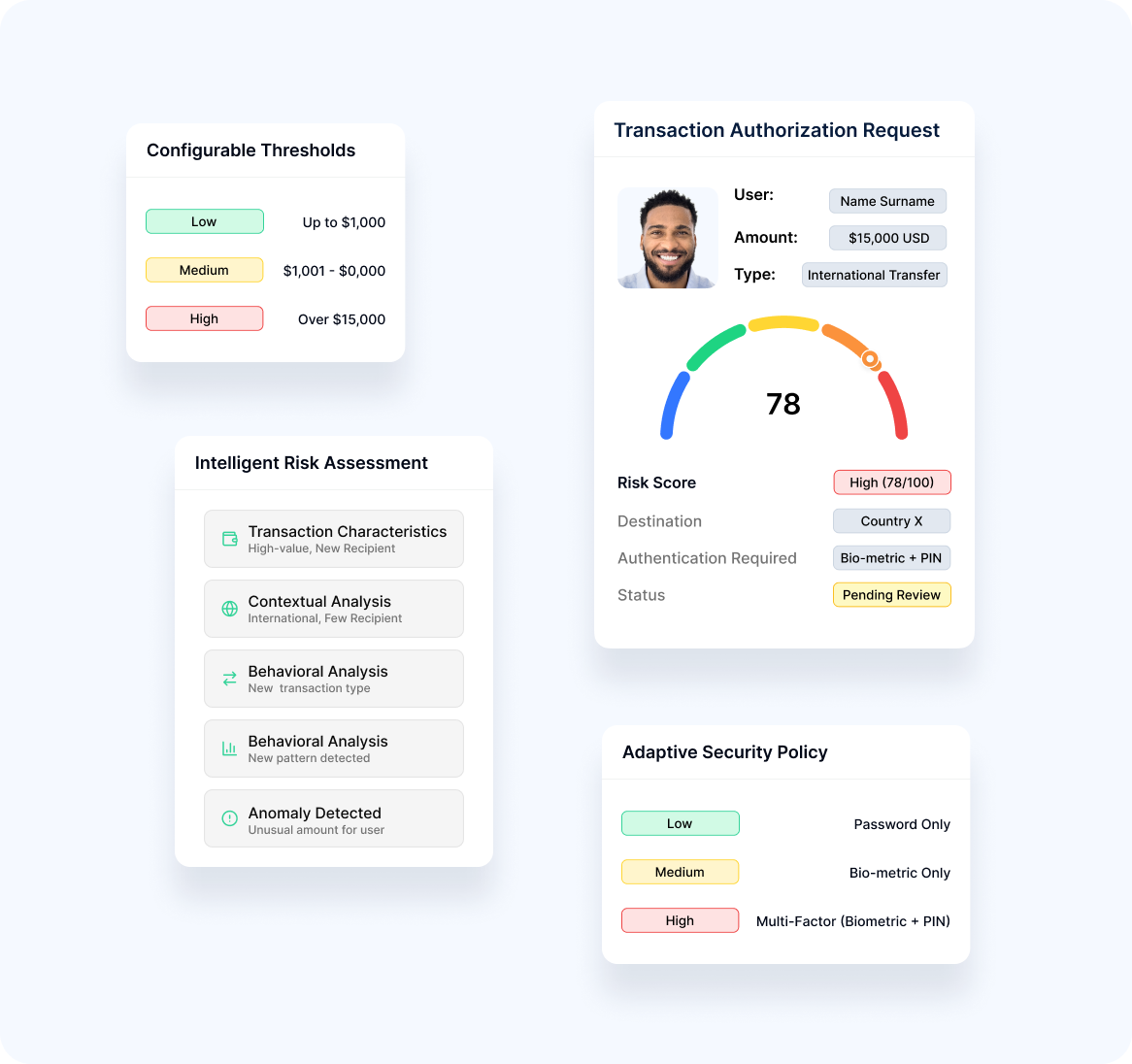
Risk-Based Authorization
Our solution applies appropriate security based on transaction risk:
Dynamic Protection
- Intelligent Risk AnalysisAnalysis of transaction characteristics and context
- Adaptive SecurityAuthentication strength proportional to risk level
- Configurable Risk ThresholdsCustomizable settings based on organization risk appetite
- Behavioral AnalysisConsideration of user patterns in risk evaluation
- Anomaly DetectionIdentification of transactions that deviate from normal patterns
Application Scenarios
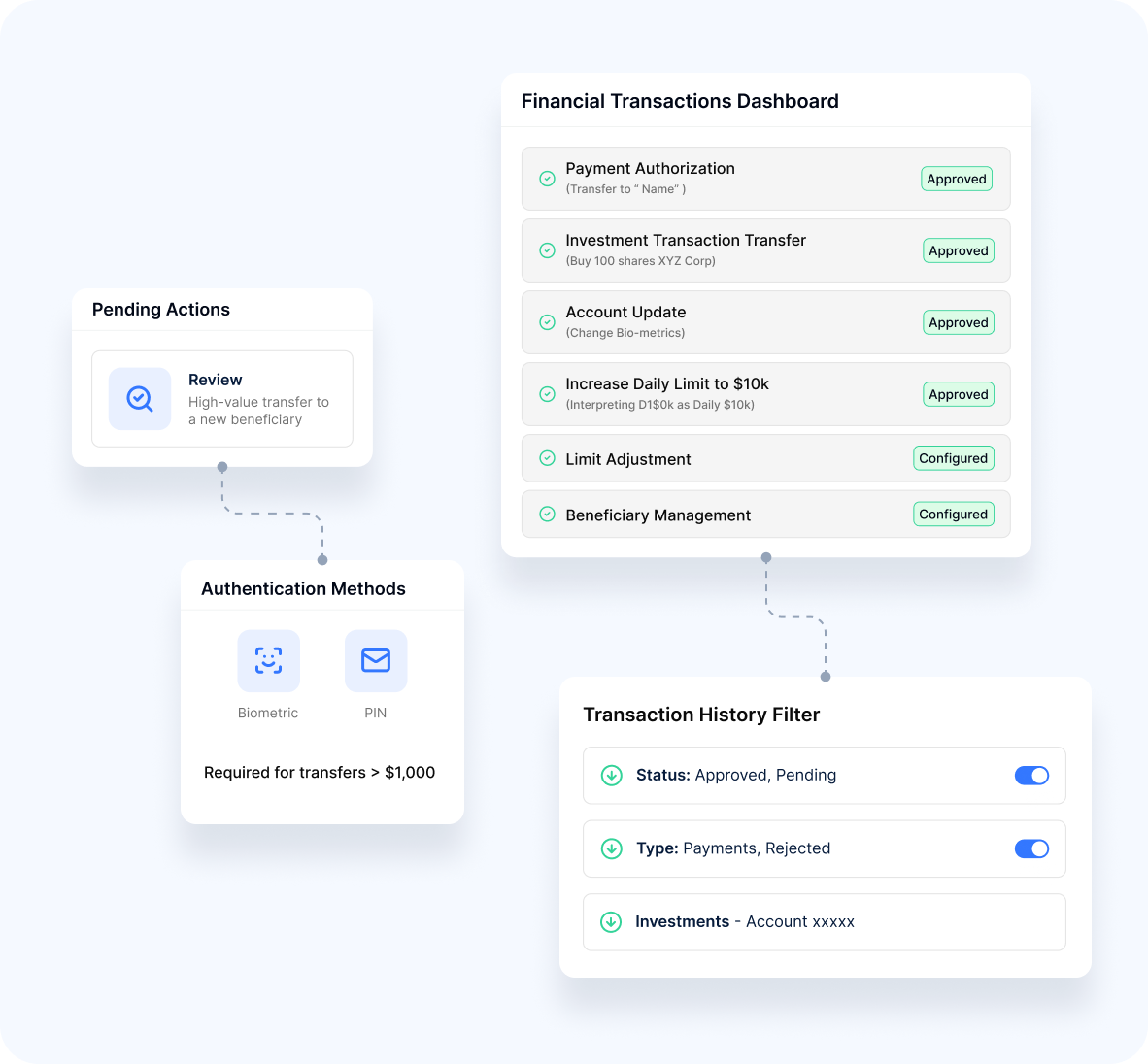
Financial Transactions
Our platform secures monetary operations:
Safe Transactions
- Payment AuthorizationPayment verification for funds transfers and purchases
- Investment TransactionsProtection for securities trading and wealth management
- Account UpdatesSecure modification of payment methods and account details
- Limit AdjustmentsSafe changes to transaction thresholds and restrictions
- Beneficiary ManagementProtected addition and modification of payment recipients
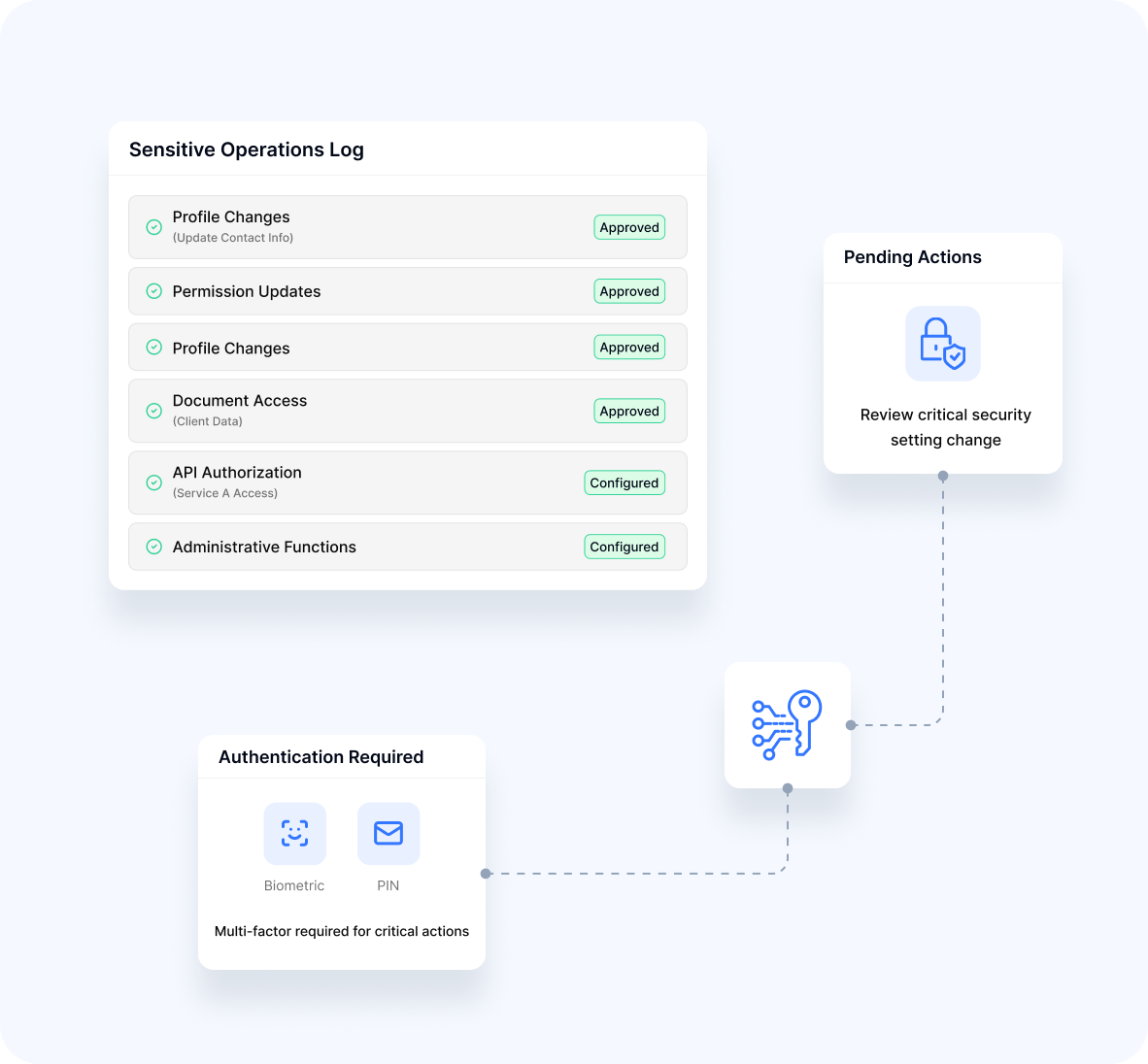
Sensitive Operations
- Profile ChangesVerification for modification of important account information
- Permission UpdatesProtection for security setting changes
- Document AccessControlled retrieval of sensitive information
- API AuthorizationSecured access to critical system interfaces
- Administrative FunctionsProtected high-impact operations
User Experience Excellence
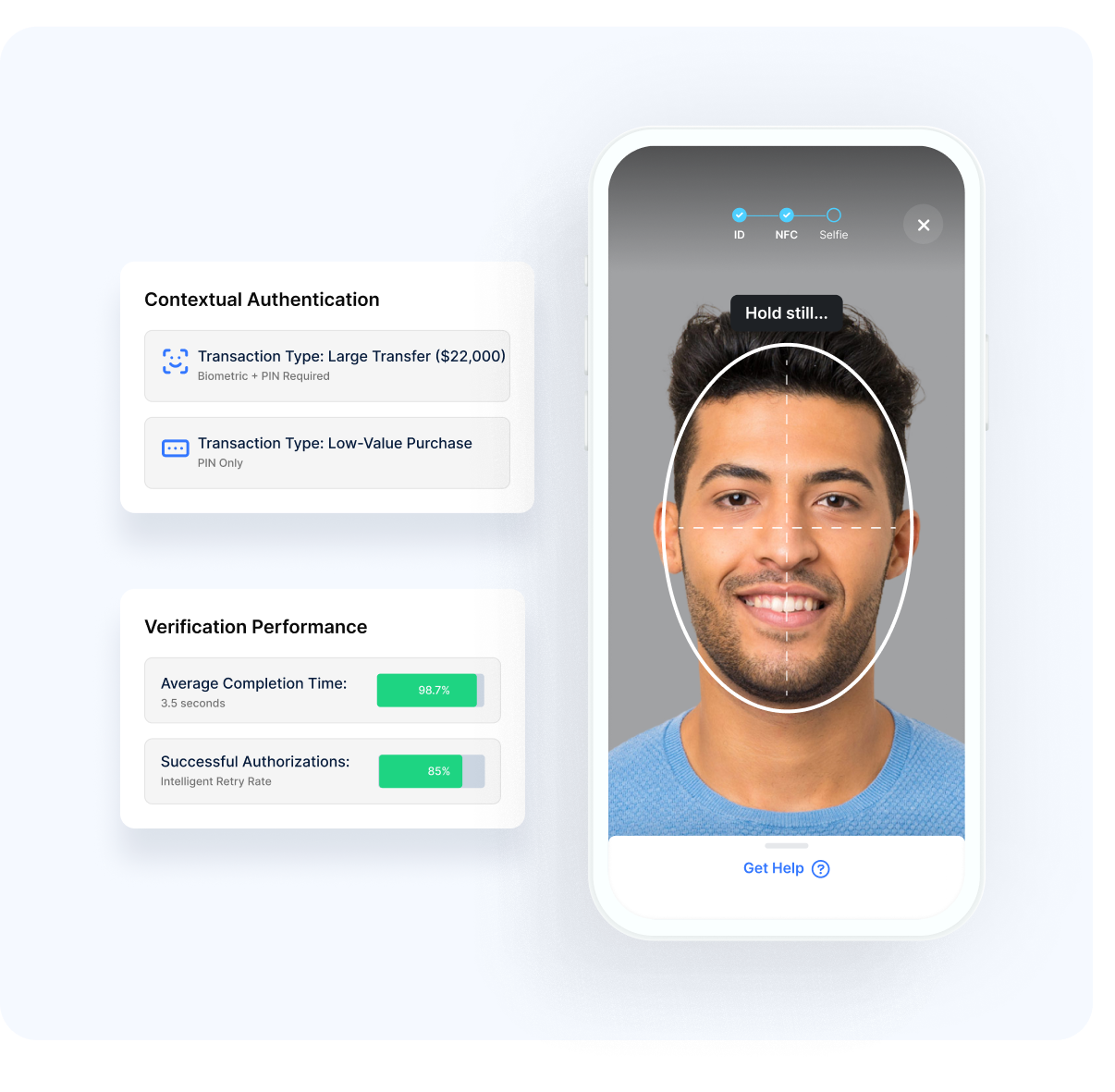
Frictionless Security
Our approach balances protection with usability:
Effortless Protection
- Contextual AuthenticationSecurity appropriate to the specific transaction
- Streamlined VerificationMinimal steps for transaction completion
- Clear Security CommunicationTransparent explanation of verification requirements
- Consistent ExperienceUniform process across channels and transaction types
- Intelligent Retry HandlingGraceful management of verification challenges
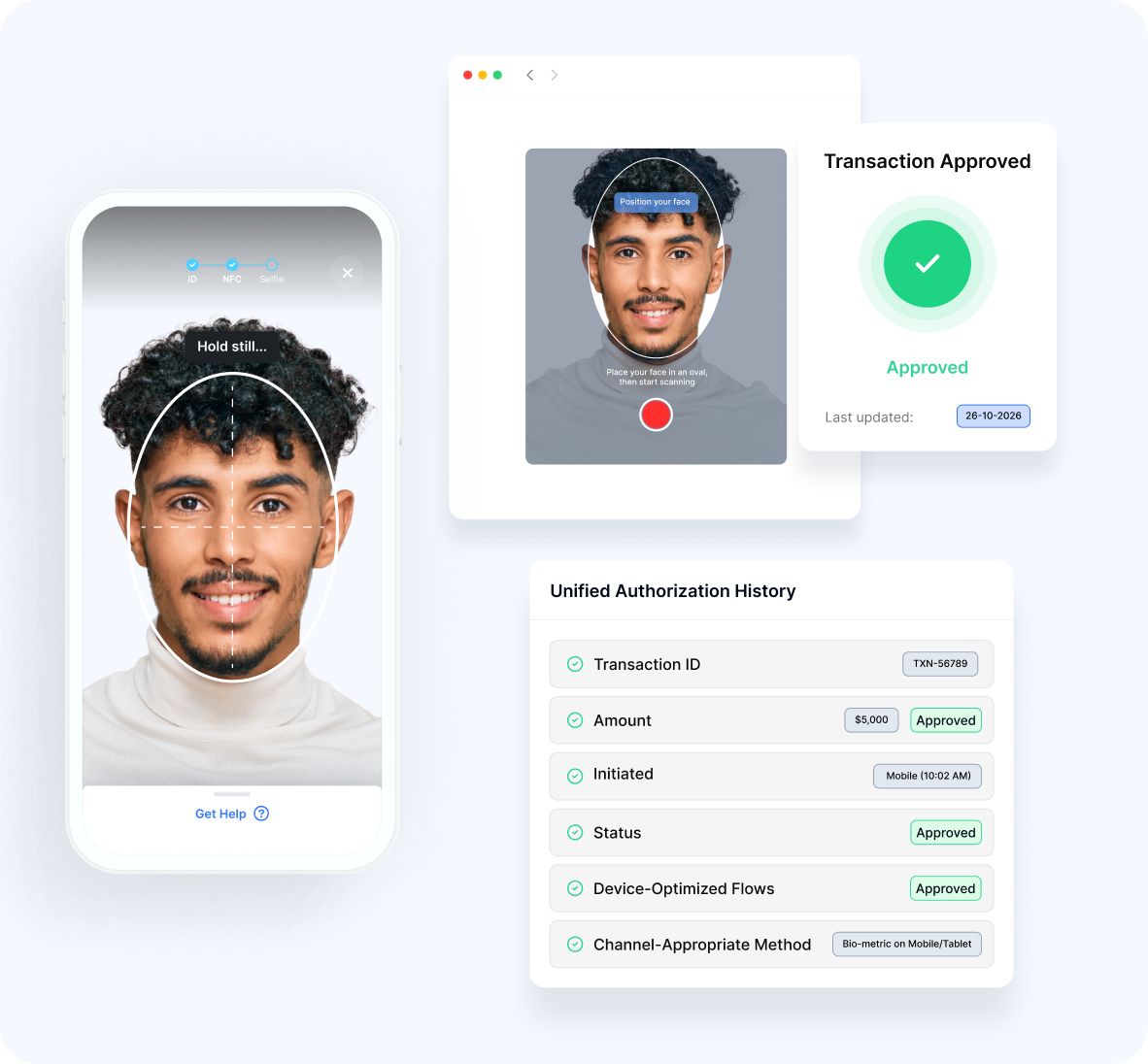
Cross-Channel Consistency
- Omnichannel SupportConsistent verification across web, mobile, and other channels
- Device-Optimized FlowsExperiences tailored to specific form factors
- Continuous SessionsSeamless transitions between devices during transactions
- Unified HistoryConsolidated view of authorized transactions
- Channel-Appropriate MethodsVerification techniques suited to each environment
Security Features
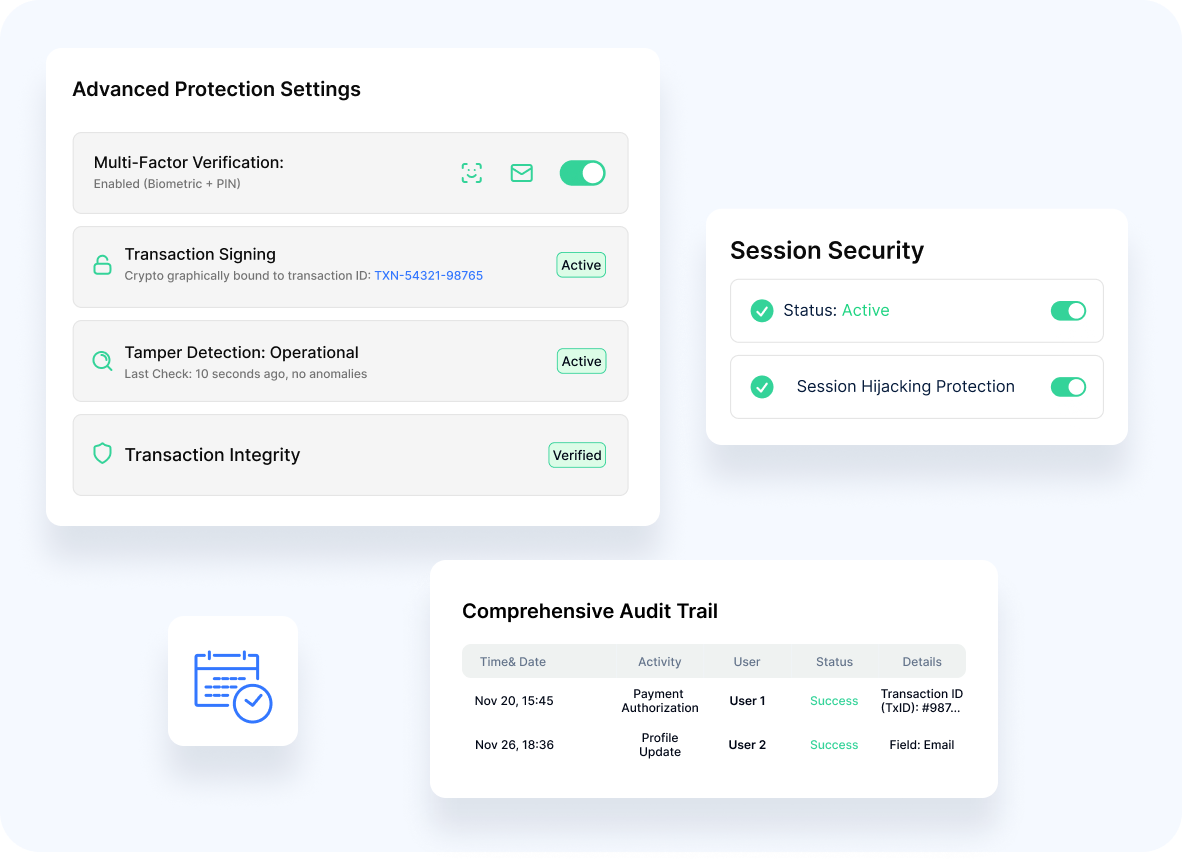
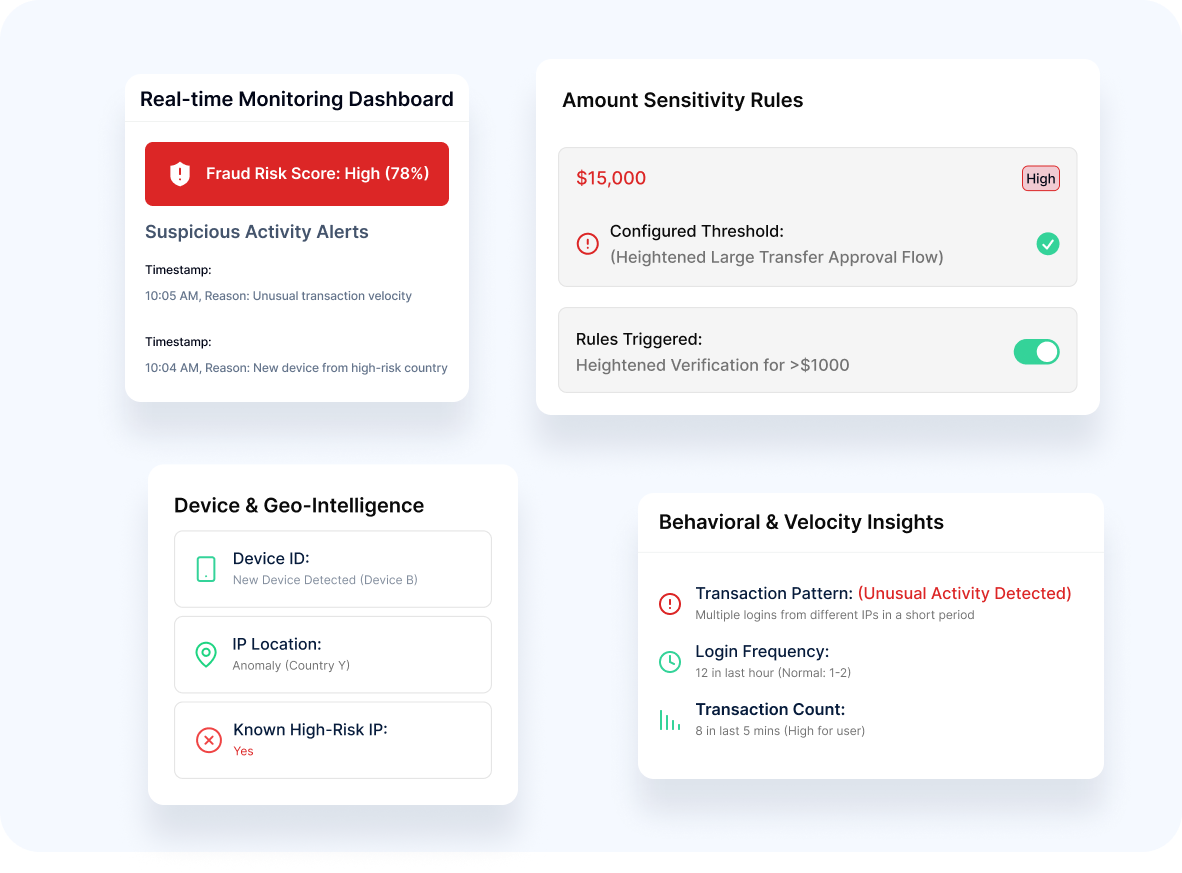
- Advanced Protection
- Fraud Detection
Our platform implements comprehensive transaction safeguards:
Multi-Factor Verification
A Combination of multiple authentication elements
Transaction Signing
Cryptographic binding of authentication to specific transactions
Tamper Detection
Identification of manipulation attempts
Session Security
Protection against session hijacking and injection
Comprehensive Audit Trail
Detailed logging of all authorization activities
Our technology offers sophisticated defense against deception:
- Pattern Analysis Detection of unusual transaction behavior
- Velocity Monitoring Identification of suspicious transaction frequency
- Device Intelligence Consideration of device characteristics and history
- Location Awareness Geographic risk factor assessment
- Amount Sensitivity Heightened verification for larger transactions
Implementation Options
Flexible Integration
Our platform supports diverse deployment approaches:
Mobile SDK
- Native libraries for iOS and Android applications
Web Components
- Pre-built UI elements for web authorization flows
API Integration
- Headless implementation for custom interfaces
Authentication Orchestration
- Incorporation into broader security frameworks
Backend Verification
- Server-side validation options
Enterprise Readiness
Our solution meets the needs of complex organizations:
Customizable Policies
- Tailored rules for different transaction types
Regulatory Alignment
- Compliance with PSD2, SCA, and other frameworks
Performance Optimization
- Minimal latency for time-sensitive transactions
High Availability Design
- Reliable operation for critical business functions
Analytics Dashboard
- Visibility into authorization patterns and security incidents

Advantage
Our transaction authorization capabilities deliver distinctive benefits:
Biometric Precision
Superior facial recognition for confident verification
Balanced Security Model
Strong protection without excessive friction
Mobile-First Design
Optimized for smartphone authorization experiences
Integration with Identity Platform
Seamless connection with broader verification ecosystem
Regional Expertise
Understanding of MEA-specific transaction security requirements
Protect high-value transactions while maintaining exceptional user experiences.
To discuss implementation options tailored to your organization's needs.
Privacy Overview
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-advertisement | 1 year | Advertisement cookies are used to provide visitors with relevant ads and marketing campaigns. These cookies track visitors across websites and collect information to provide customized ads. |
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |

Please wait while you are redirected to the right page...