Table Of Contents
- Authentication – A brief overview
- What is an authentication factor?
- What is authentication used for?
- What are the common methods of authentication?
- How does authentication vary from authorization?
- What are the features of uqudo’s authentication process?
- How does uqudo’s authentication system work?
- Why choose uqudo for your organization’s seamless authentication process?
Authentication – A brief overview
Authentication refers to the process of determining if the identity provided by a user is valid. This technology helps in putting in place an access control system where only authenticated individuals can access confidential information. Authentication is used by a client or a server when they need to know who has access to their systems and also control the type of access.
With the world today heavily dependent on technology where personal information like address and bank account information can be easily obtained from an individual’s personal device, it is necessary that all this data is made secure. This can only be done by using different levels of authentication.
To authenticate a user, credentials are generally required, which then gives them access to a particular piece of information. An example of this would be signing in to an email account. For this, the user has to provide a username and then sign in using their login credentials. The email server then verifies the information provided with their internal repository and allows the user access if the credentials are valid.
The most common method of authentication is that of a self-selected password a user enters while creating an account that provides access to the system. With an increase in online fraud and a growing need for cybersecurity, using a password is no longer the safest way to authenticate a user. Different types of authentication are common nowadays and they include two-factor authentication, biometrics, facial recognition, CAPTCHAs, and many more.
The more secure an organization’s authentication process is, the more protected the company data is from security breaches and cyber-attacks. In order to comply with the government’s AML regulations, it is necessary for banks and financial institutions to have a highly stringent authentication process in place.
What is an authentication factor?
An authentication factor refers to a piece of information used to verify and authenticate the identity of an individual trying to get access to or requesting data from a secured network, system, or application. Each authentication factor varies according to the level of security it provides. The ultimate goal of each of these factors is to allow only authorized users access to a particular system.
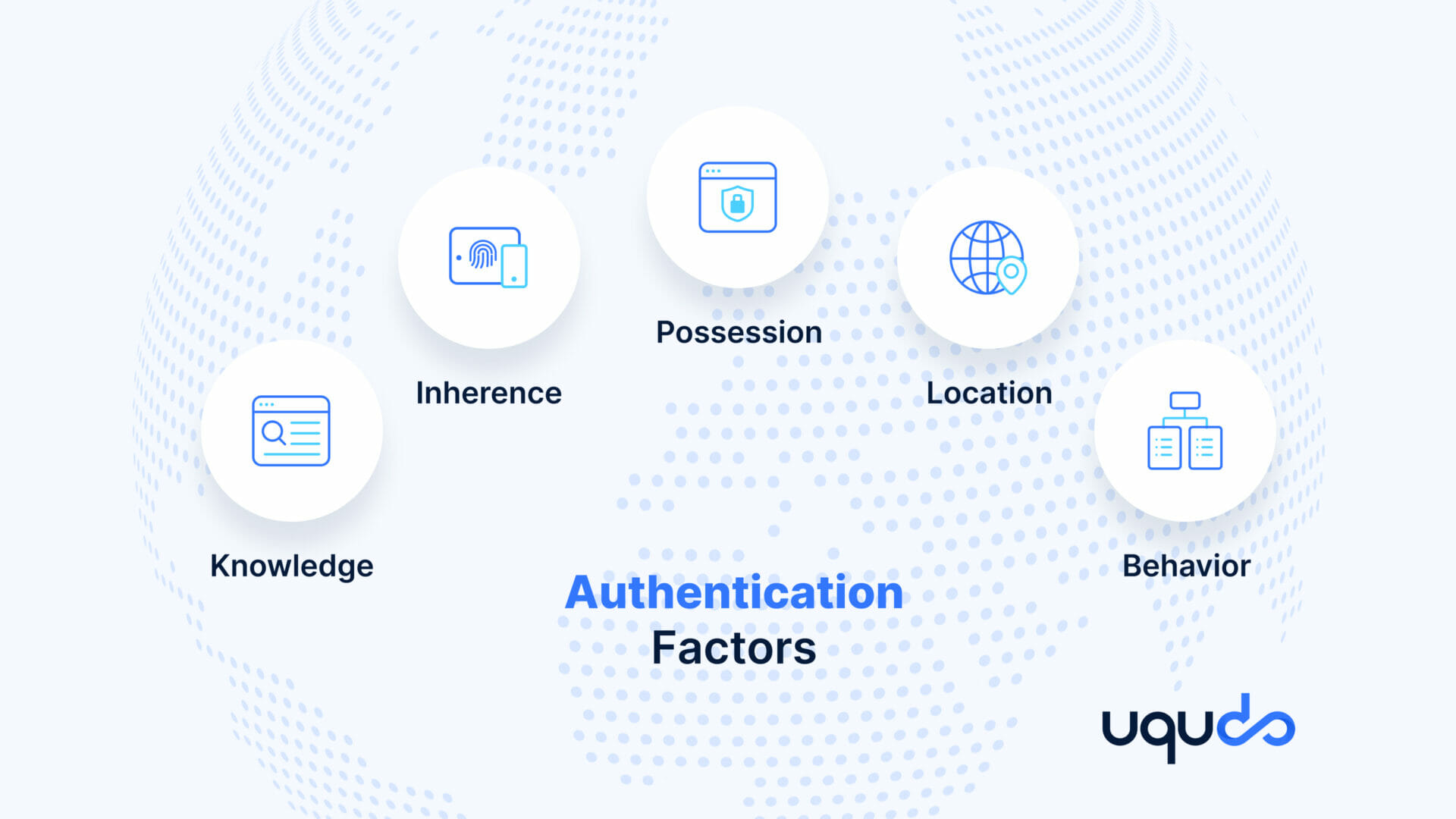
- Knowledge factor
A knowledge factor is a type of authentication factor that is often called as something the user knows and is perhaps the most commonly used type of authentication. For this, a user has to provide some data before they are granted access to the system, which generally is a password or a PIN code. This information is generally created by the user themselves and is stored in the Identity Access Management (IAM) system. - Inherence factor
Inherence factor refers to using an individual’s inherent traits for authentication. This is also known as something the user is and includes biometric information like fingerprint scans, facial recognition, voice recognition, retina, and iris scans. Inherence factors are one of the most secure methods of authentication, but it is necessary for the device to have a built-in biometric system. - Possession factor
Possession factor refers to something the user has and includes a specific piece of information or device. Possession factors are identified as items that typically belong to the user like a mobile device or an email. In this, a One Time Password (OTP) is sent to the user’s email address or phone device and is secure because they generally expire after a short period of time. - Location factor
This is also referred to as somewhere the user is and refers to the identification of the user’s location prior to approving access to secure systems. This method of authentication comes into effect when a user is trying to access a secure system from a location that is either a different country or is somewhat distant from the usual access location. - Behaviour factor
Behaviour-based authentication, also known as something the user does refers to verifying the identity of a user based on their behavioural patterns. An example of this would be identifying a user based on their digital behaviour like their typing pattern. Unlike other methods of authentication, biometric authentication occurs on a real-time basis.
What is authentication used for?
With the evolution of technology in a manner that has made simple tasks such as ordering food or renting a car as well as complex activities like paying off loans or credit card bills completely online, it is necessary to have a system in place that prevents unauthorized users from accessing secure data. The increase in online transactions has however made the protection of critical information quite difficult, making banks and financial institutions vulnerable to numerous cyber attacks and financial crimes. This has made authentication very important for every industry trying to safeguard their confidential information.
Authenticating a user is crucial for preventing unauthorized access to private information because a weak authentication process makes it easy for cybercriminals to breach the system and gain unauthorized access. According to IBM, the overall cost of data breaches in 2021 was $ 4.24 million. This means that the absence of a secure system can prove very costly to the fintech industry, and greater effort has to be taken to protect data. Companies that invest in a full-fledged IAM system get numerous benefits, including
- Lesser number of data breaches due to identity theft
- Improves their user’s experience
- Reduction in long-term operational costs
- Greater compliance with cyber laws
What are the common methods of authentication?
Authentication is the first line of defence against cyber attacks and helps systems identify if an individual is the same as they are showing themselves to be. Authentication factors are often used in combinations to provide a higher level of security.
- Single-factor authentication
The simplest method of authentication, single-factor authentication requires a single credential to provide the user access to the system. A common example of SFA is password/PIN-based authentication. Even though SFA is user-friendly (due to the ease of remembering a single password), it is relatively easy for cyber criminals to get through. The security of this method depends on the user who has created the password; the tougher the password is to crack, the safer the system is. - Two-factor authentication
Adding a second layer of authentication increases the security of a system to a large extent. It is a combination of the factors ‘something you know’ and ‘something you have’, which means that for 2FA, a user is first asked their password and then a security OTP that goes to their device via an app or through text. This added level of security protects criminals from getting access to confidential data. The only shortcoming to 2FA is that the user needs to always have access to a particular device while authorizing their access. - Multi-factor authentication
For multi-factor authentication, users are asked to verify their identity by successfully presenting two or more pieces of information. 2FA is in fact a subset of multi-factor authentication where a user has to input 2 factors for authenticating themselves. MFA uses a combination of passwords, security questions, OTPs, or biometrics for user authentication. - Biometric authentication
The biometric method of authentication relies on the physical traits of an individual to authenticate their credentials. This is done by comparing a user’s biometric characteristics like facial features, fingerprints, or retina against a stored sample. Biometric authentication is a relatively safer method to authenticate a user, but the main challenges, in this case, lie in the specific type of hardware required for biometric purposes. - Transaction authentication
Transaction authentication is a type of authentication used by some banks and financial institutions to authenticate if a particular transaction is done by the account holder or not. For this, an OTP is sent to the user for that particular transaction which is then authenticated by the transaction network. - Token-based authentication
In this method, a user has to verify their credentials the first time they log in, and after verification, they are provided with a token using which the user can get access to particular resources for a certain period of time. - Single sign-on
Single sign-on (SSO) is a type of authentication in which an individual uses a single set of credentials to log in to several independent applications. This is generally done in small enterprises so that the user does not have to enter their credentials every time they need to access something on the system. An example of this would be logging in to a Gmail account and then having access to other Google services like YouTube and Google drive.
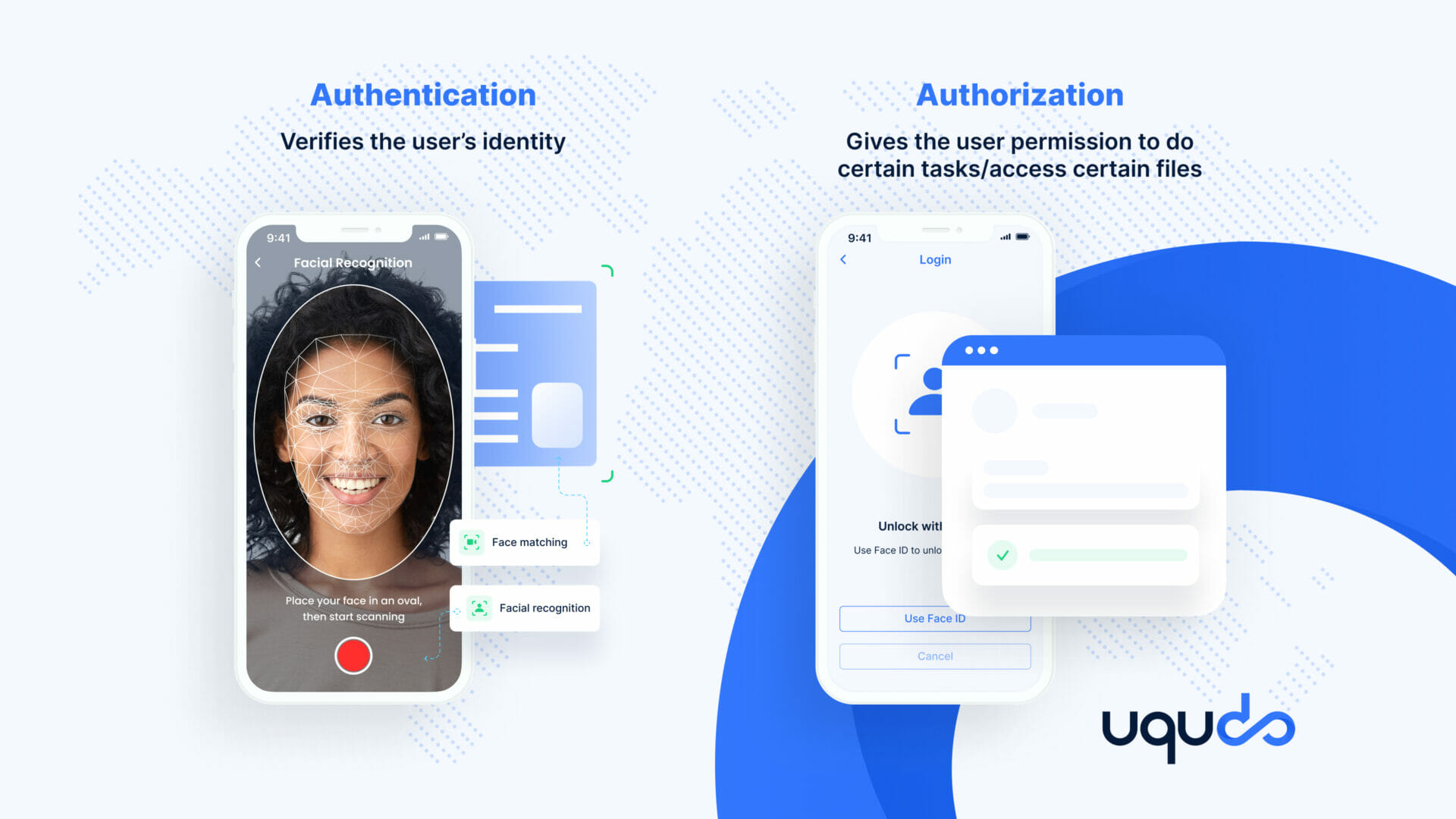
How does authentication vary from authorization?
With the growing need for digital security in the world of technological advancement, the need for stringent authentication and authorization procedures in an organization is very high. Though both these terms are often used interchangeably, they refer to two different procedures. In the world of Digital Identity, authentication refers to verifying the identity of a user, whereas authorization refers to validating of a user has permission to access certain files, data, and applications. Both authentication and authorization help system managers control who has what kind of access to resources in a system.
After a user has been authenticated to access files in a system, the user has to be authorized in order to determine if they are allowed partial or full access to certain files. The authorization policy of a system determines what a user can do. For example, an employee has to first authenticate themselves while trying to access the company’s system software. After successful authentication, the employee can access only those files which the system administrator has authorized them to access.
What are the features of uqudo’s authentication process?
uqudo’s authentication process uses state-of-the-art biometrics for passwordless login, multi-factor authentication, account recovery, transaction authorization, and more.
- Passwordless login
As the term indicates, passwordless login refers to user authentication without the hassle of using a password and using other methods like verifying credentials using a secondary device, biometrics, or OTPs for authenticating a user. - Biometric Authentication
A comprehensive biometric authentication solution is another important feature of uqudo’s authentication process. In this, users are verified using specific physical features such as facial recognition, fingerprint scans, retina, and iris recognition. Since biometrics are hard to replicate, this solution is very secure. - Two-Factor Authentication
2FA adds a second layer of authentication while verifying a user’s identity. uqudo’s two-factor authentication service uses facial recognition as the second factor, making it very difficult to be stolen by identity thieves. - FIDO & FIDO2 Authentication
uqudo uses Fast Identity Online for an extra secure authentication process. FIDO2 represents a passwordless authentication process on top of an existing two-factor authentication, making the system even more secure. uqudo’s FIDO2 authentication services use a combination of authentication and cryptography making our passwordless authentication services very safe. - Account Recovery
When a user is unable to authenticate themselves for whatever reason they have to recover their account through a number of steps. Generally, a user has to answer various questions or validate themselves through numerous OTPs to recover their account. However, uqudo’s account recovery solutions involve easier steps like face, fingerprint, or voice verification to authenticate the account owner. - Transactional authorization
Transactional authorization is an important step for authorization of an online transaction, to check if a transaction has been done by the authorized bank account holder or not. uqudo’s transactional authorization services verify sensitive operations for banking systems using time-based OTPs or biometric sign-ins.
How does uqudo’s authentication system work?
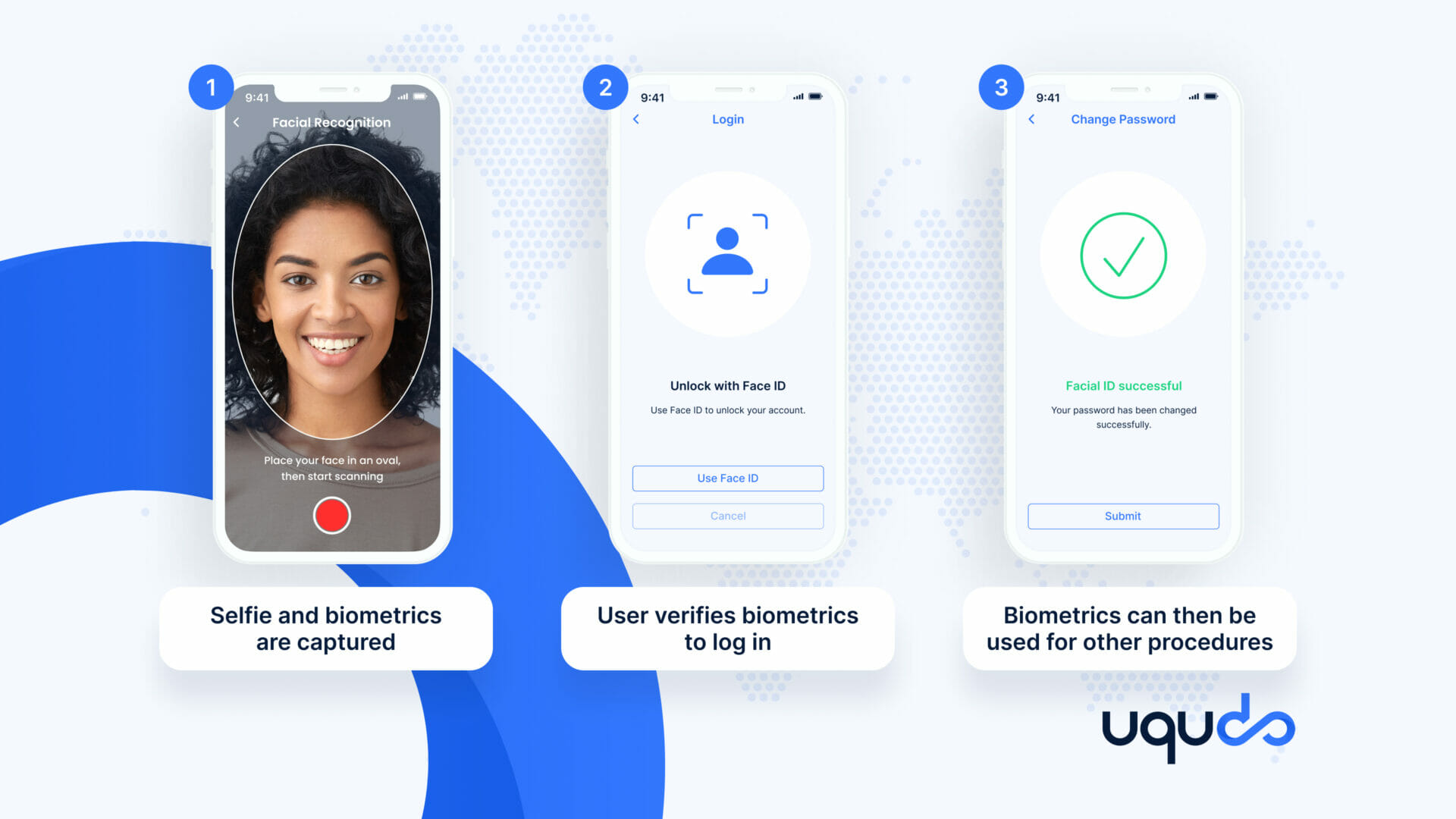
uqudo’s fast and highly secure authentication procedure involves the following steps:
- A selfie of the user and biometric data is captured during the signing-up process.
- For logging in, the user has to simply verify their biometrics
- The captured biometric can then be used for two-factor authentication, account recovery, and transaction authentication.
Why choose uqudo for your organization’s seamless authentication process?
- uqudo’s impeccable authentication helps enhance your user experience with fast and frictionless logins.
- Our stringent authentication policy eliminates the chances of stolen identities due to weak or misused passwords.
- Our easy-to-implement authentication protocols eliminate your need for extensive IT support for everyday authentication processes.
- To reduce the hassle of constant log-ins, our ongoing KYC procedures can help authenticate your future transactions.
To learn more about this, please get in touch with us.


