Face Verification and Liveness Detection
Protect against stolen identities with liveness-based facial recognition
Measure and match unique characteristics to authenticate
users and keep bad actors away.
See it in action:
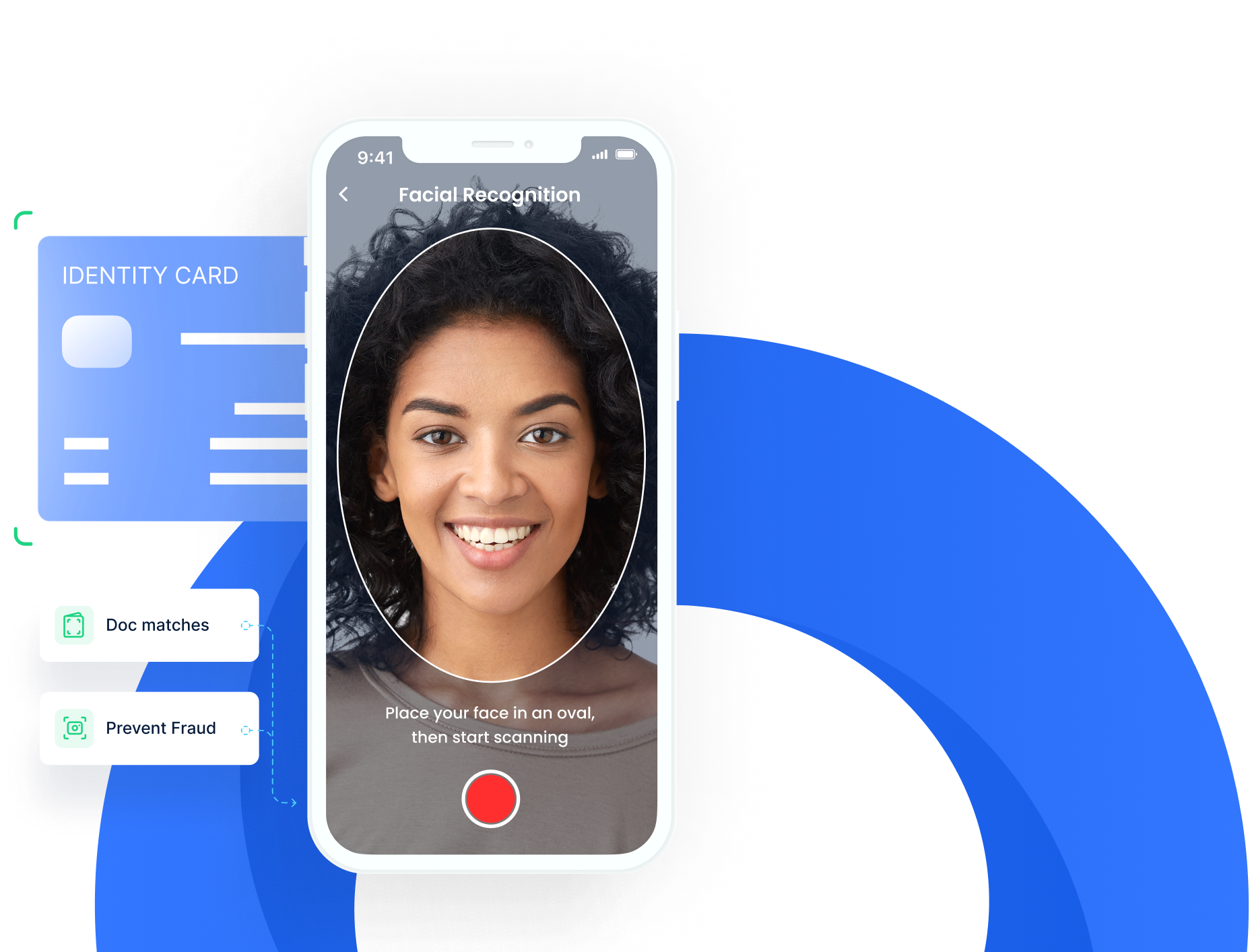
Why choose us?
Non-invasive verification
Eliminate the need for your users to remember passwords with a non-intrusive digital facial recognition.
Faster processing
Recognise faces in a second to quickly and efficiently validate a person’s identity.
Enhance UX
Use AI and deep learning to extract data and automate repetitive tasks, enhancing user experience.
Data security
All your biometric data is encrypted and protected from misuse.
How it works?
Step 1
Capture the face image using any standard camera.
Step 2
Analyse the captured face image to identify key nodal points.
Step 3
Detect liveness by using a texture-based algorithm.
Step 4
Convert extracted facial images to data.
Face Verification Features

Face Detection
- Detect the user’s image and capture it using a standard camera on the onboarding mobile app.
- Human face detection is done using algorithms and machine learning.
- The algorithm detects facial features which are analysed in the next step.
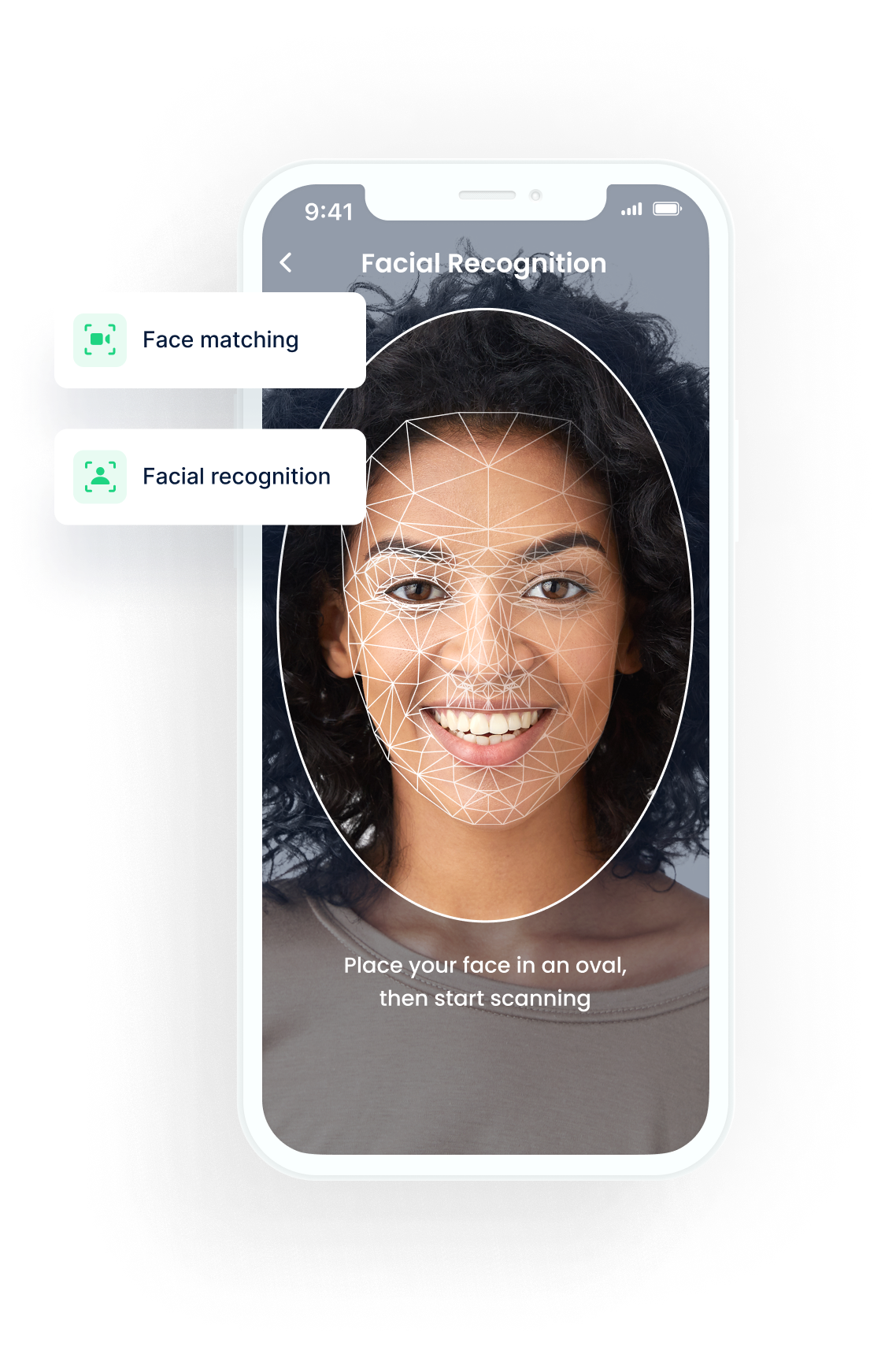
Face Analysis
- The captured image is then analysed.
- A combination of computer vision, machine learning and image processing solutions are used to analyse facial features.
- The software identifies the nodal points, which are the distances between facial features, to identify key facial landmarks.
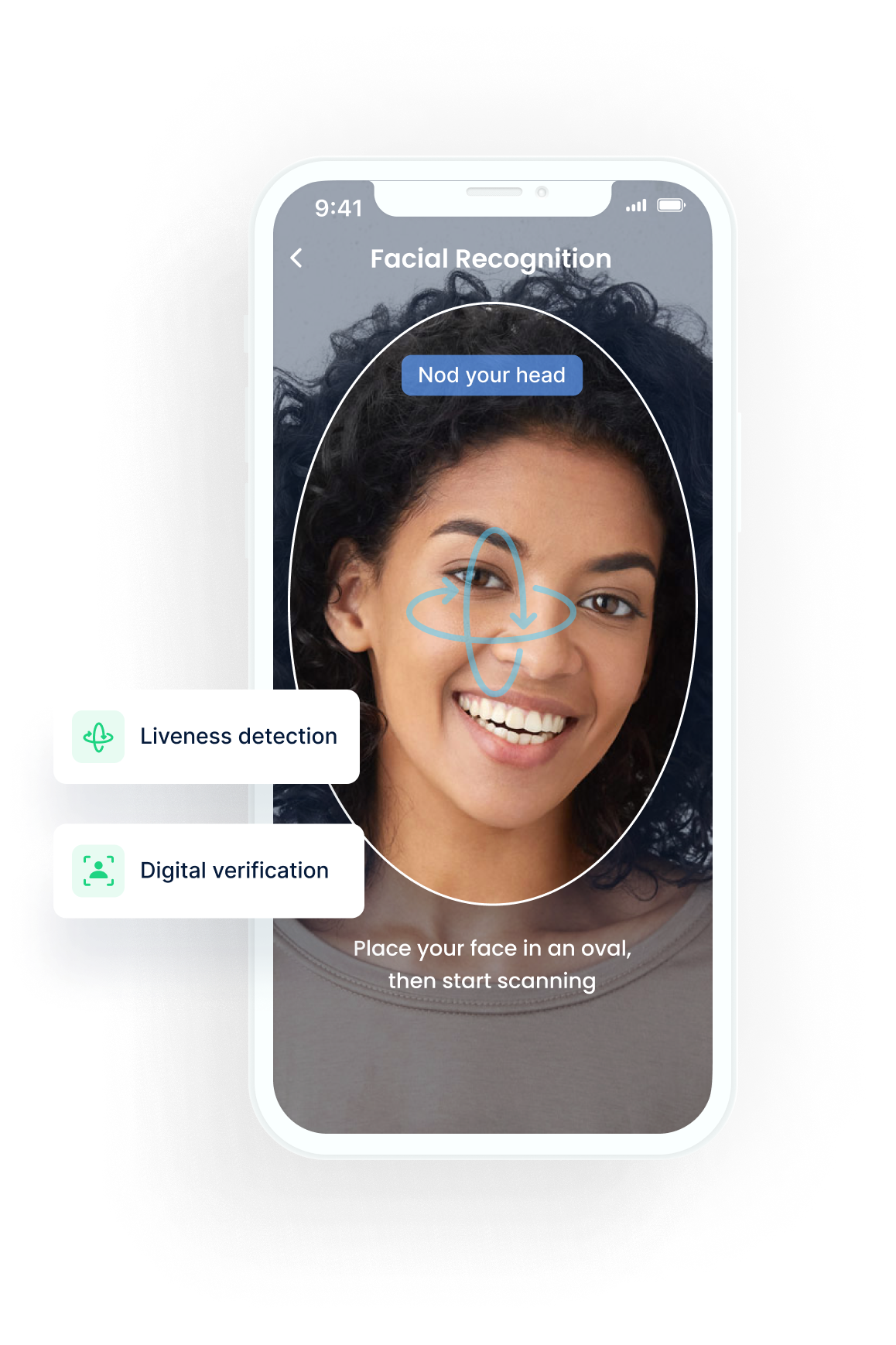
Liveness Detection
- The user is then guided to turn their head in randomised directions to evaluate their liveness.
- Liveness detection is done using special computer vision technology to check if the person is real.
- Liveness detection helps identify spoofs and maximises accuracy during identity verification.

Evaluation of facial data
- After liveness evaluation, the data is sent to the server.
- In the case of a new user, this data is used for user onboarding.
- For an already existing customer, the data is digitally authenticated for signing in.
Secure, frictionless, & fully compliant digital onboarding. Integrated seamlessly within your app.

What is KYC? Overview, Uses, Components and Process
Chandrika Mahapatra
KYC Content Specialist uqudo
4 reasons why is KYC broken and how you can achieve better compliance
Chandrika Mahapatra
KYC Content Specialist uqudo
How facial recognition is changing digital identity?
Chandrika Mahapatra
KYC Content Specialist uqudo
Our clients
Easily integrate  with your tech stack.
with your tech stack.
Use our simple and secure Web SDK, Mobile SDK, or RESTful API to seamlessly integrate identity capabilities into your operations.
See documentationAn award-winning team
uqudo is proud to be recognised by some of the world’s most distinguished organisations.
We price based on successful onboarding.
Say goodbye to request-based fees, repeat charges, and spiralling customer acquisition costs.
FAQ
What is KYC?
Know Your Customer (KYC) is an identity verification process that authenticates the real identity of customers during onboarding.
What is Enhanced Due Diligence?
EDD goes beyond CDD and looks to establish a higher level of identity assurance with additional verification steps such as verifying the customer’s address.
How do you perform KYC?
Three key steps are involved in our identity process; first, we read the document and extract identity data; next, we check the person on camera is real and matches the document; finally, we verify document authenticity via government databases or using the digital signatures on the document.
What are the requirements for KYC?
KYC document requirements vary according to a region’s jurisdiction but generally include
- A government-issued ID card
- Passport
- Driving License
- Voter’s ID
- Birth certificates
Why is KYC required?
KYC helps financial institutions verify the identity of customers and prevents companies from being used in illegal financial activities. KYC also helps firms understand their customer’s financial behaviour, aiding in a better user experience.
Is facial recognition safe?
Biometric face authentication uses unique facial patterns to identify people, making it highly efficient. Since our platform doesn’t store data, all biometric information is encrypted and secure.
Privacy Overview
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-advertisement | 1 year | Advertisement cookies are used to provide visitors with relevant ads and marketing campaigns. These cookies track visitors across websites and collect information to provide customized ads. |
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |

Please wait while you are redirected to the right page...
















 with your tech stack.
with your tech stack.








